The cybersecurity landscape has undergone a dramatic transformation with the integration of artificial intelligence into vulnerability scanning and threat detection systems. Traditional security assessment methods, while foundational, often struggle to keep pace with the rapidly evolving threat landscape and the increasing complexity of modern software architectures. AI-driven security vulnerability scanning represents a paradigm shift that leverages machine learning algorithms, pattern recognition, and intelligent automation to identify, analyze, and prioritize security weaknesses with unprecedented accuracy and efficiency.
Stay updated with the latest AI security developments as the intersection of artificial intelligence and cybersecurity continues to evolve at breakneck speed. The convergence of these technologies has created powerful defensive capabilities that can anticipate, detect, and respond to security threats in ways that were previously impossible with conventional security tools and methodologies.
The Evolution of Security Vulnerability Assessment
The traditional approach to vulnerability scanning has relied heavily on signature-based detection systems, rule-based engines, and manual security assessments conducted by cybersecurity professionals. While these methods have served as the backbone of organizational security for decades, they possess inherent limitations that become increasingly apparent in today’s dynamic threat environment. Static vulnerability databases, limited pattern recognition capabilities, and the reactive nature of traditional scanning tools often result in delayed threat detection and high rates of false positives that overwhelm security teams.
AI-driven vulnerability scanning addresses these challenges through sophisticated machine learning algorithms that can learn from vast datasets of security incidents, code patterns, and attack vectors. These systems continuously evolve their detection capabilities, adapting to new threats and attack methodologies without requiring manual updates to signature databases or rule sets. The result is a more proactive, accurate, and comprehensive approach to security assessment that can identify zero-day vulnerabilities, detect subtle attack patterns, and provide contextual risk analysis that enables better security decision-making.
Machine Learning Foundations in Security Scanning
The effectiveness of AI-driven vulnerability scanning stems from its foundation in advanced machine learning techniques specifically adapted for cybersecurity applications. Deep learning neural networks excel at identifying complex patterns in code structures, network traffic, and system behaviors that may indicate security vulnerabilities or ongoing attacks. These systems can analyze millions of lines of code, network packets, and system logs simultaneously, identifying subtle anomalies and correlations that would be impossible for human analysts to detect manually.
Natural language processing capabilities enable AI security systems to parse and understand security advisories, threat intelligence reports, and vulnerability databases from multiple sources, automatically correlating this information with detected vulnerabilities to provide comprehensive threat context. Computer vision techniques applied to network topology analysis and system architecture visualization help identify potential attack paths and security misconfigurations that traditional scanning tools might overlook.
Enhance your security analysis with advanced AI tools like Claude that can provide detailed code analysis, security pattern recognition, and comprehensive vulnerability assessment guidance. The integration of multiple AI technologies creates a holistic security assessment platform that addresses both technical vulnerabilities and strategic security considerations.
Automated Code Analysis and Static Application Security Testing
One of the most significant applications of AI in vulnerability scanning lies in automated code analysis and static application security testing (SAST). Traditional static analysis tools rely on predefined rules and signatures to identify potential security flaws, often producing numerous false positives and missing subtle vulnerabilities that don’t match known patterns. AI-enhanced SAST tools utilize machine learning models trained on vast repositories of vulnerable and secure code to understand the contextual relationships between code components, data flows, and potential attack vectors.
These intelligent systems can identify complex vulnerabilities such as injection attacks, authentication bypasses, and privilege escalation opportunities by analyzing code semantics rather than just syntactic patterns. The AI models understand the intent behind code structures, enabling them to detect vulnerabilities that emerge from the interaction between multiple code components or arise from subtle logical flaws that traditional tools might miss. Additionally, AI-driven code analysis can prioritize vulnerabilities based on exploitability, business impact, and the likelihood of successful attacks, helping development teams focus their remediation efforts on the most critical security issues.
Dynamic Application Security Testing Enhancement
Dynamic application security testing (DAST) has been revolutionized through AI integration, transforming it from a reactive testing methodology into an intelligent, adaptive security assessment platform. Traditional DAST tools follow predefined test sequences and attack patterns, often missing application-specific vulnerabilities or failing to adapt their testing strategies based on application behavior. AI-enhanced DAST systems employ reinforcement learning algorithms that can dynamically adjust their testing approaches based on application responses, discovered vulnerabilities, and emerging threat patterns.
These intelligent testing systems can automatically generate custom payloads, adapt their attack strategies to specific application architectures, and identify complex multi-step attack sequences that would require extensive manual configuration in traditional tools. Machine learning algorithms analyze application responses to various inputs, identifying subtle behavioral patterns that may indicate underlying vulnerabilities even when explicit error messages or security violations are not immediately apparent.
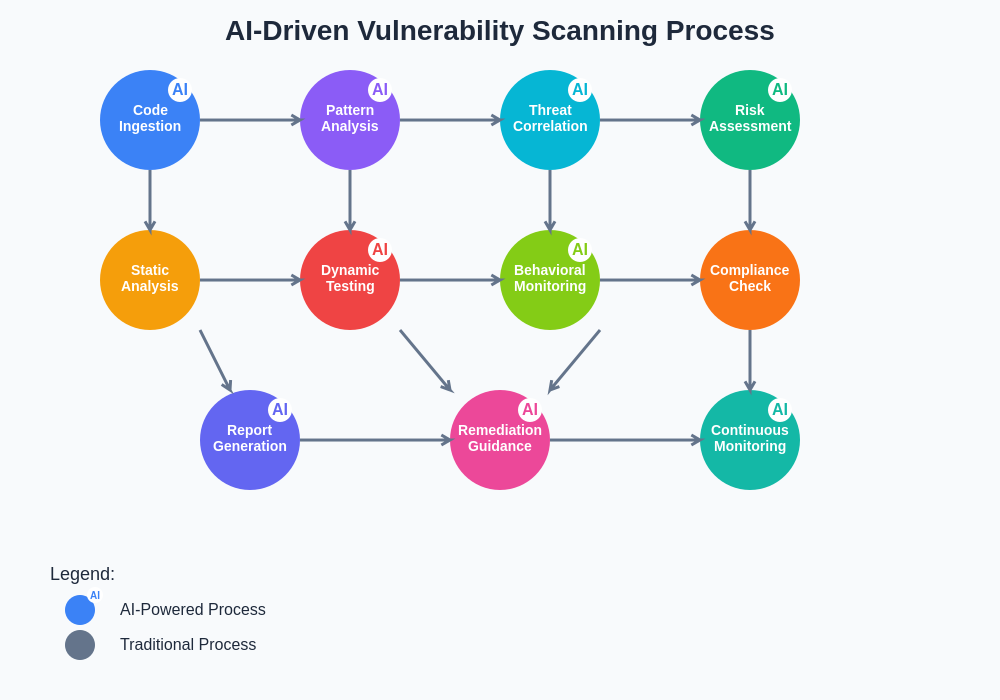
The comprehensive scanning process integrates multiple AI-powered stages that work together to provide thorough security assessment. Each stage leverages machine learning algorithms to enhance traditional security testing methodologies, creating a more intelligent and adaptive approach to vulnerability discovery and risk assessment.
Network Security and Infrastructure Vulnerability Assessment
The application of AI to network security and infrastructure vulnerability assessment has created powerful capabilities for identifying and analyzing security weaknesses across complex, distributed systems. Traditional network vulnerability scanners typically rely on port scanning, service fingerprinting, and known vulnerability databases to assess network security posture. AI-driven network security assessment tools enhance these capabilities through intelligent traffic analysis, behavioral anomaly detection, and predictive threat modeling.
Machine learning algorithms can analyze network traffic patterns, identify unusual communication flows, and detect potential indicators of compromise that might suggest ongoing attacks or security breaches. These systems can correlate vulnerability scan results with network behavior analysis, threat intelligence feeds, and historical attack patterns to provide comprehensive risk assessments that consider both technical vulnerabilities and operational security context.
Leverage comprehensive AI research capabilities with Perplexity to stay informed about emerging threat vectors, vulnerability research, and security best practices that inform effective AI-driven security strategies. The continuous evolution of both attack methodologies and defensive technologies requires ongoing research and analysis to maintain effective security postures.
Threat Intelligence Integration and Contextual Analysis
Modern AI-driven vulnerability scanning systems excel at integrating diverse threat intelligence sources to provide contextual analysis that goes far beyond simple vulnerability identification. These systems automatically correlate discovered vulnerabilities with active threat campaigns, known exploit kits, and attacker tactics, techniques, and procedures (TTPs) to assess the realistic risk posed by each identified vulnerability. Machine learning algorithms analyze patterns across multiple threat intelligence feeds, security incident reports, and vulnerability databases to identify emerging threats and predict potential attack vectors before they become widely exploited.
The contextual analysis capabilities of AI-driven systems enable organizations to move beyond simple vulnerability counting toward risk-based security management. These systems can assess the business impact of vulnerabilities based on asset criticality, data sensitivity, and operational dependencies, providing security teams with actionable intelligence that supports informed decision-making about remediation priorities and resource allocation.
Behavioral Analysis and Anomaly Detection
AI-driven security systems have revolutionized behavioral analysis and anomaly detection by establishing sophisticated baselines of normal system and user behavior, then identifying deviations that may indicate security incidents or emerging vulnerabilities. Traditional signature-based detection systems struggle with zero-day attacks and advanced persistent threats that don’t match known attack patterns. Machine learning algorithms can identify subtle behavioral anomalies that may indicate reconnaissance activities, privilege escalation attempts, or data exfiltration operations.
These behavioral analysis capabilities extend beyond simple anomaly detection to include predictive threat modeling that can anticipate potential attack paths and security vulnerabilities based on observed system behaviors and environmental changes. The systems continuously learn from new data, refining their understanding of normal operations and improving their ability to distinguish between legitimate operational variations and potentially malicious activities.
Cloud Security and Container Vulnerability Assessment
The shift toward cloud computing and containerized applications has created new security challenges that traditional vulnerability scanning tools struggle to address effectively. AI-driven cloud security assessment tools have been specifically designed to handle the dynamic, ephemeral nature of cloud environments and the complex dependencies inherent in containerized applications. These systems can automatically discover and assess cloud resources, analyze container images for vulnerabilities, and monitor runtime environments for security misconfigurations and policy violations.
Machine learning algorithms excel at understanding the complex relationships between cloud services, container dependencies, and application components, enabling comprehensive security assessment across multi-cloud and hybrid environments. The systems can identify security risks that emerge from cloud service configurations, container orchestration policies, and inter-service communication patterns, providing holistic security visibility across distributed application architectures.
Automated Penetration Testing and Red Team Operations
The integration of AI into penetration testing and red team operations has created intelligent systems capable of conducting sophisticated security assessments with minimal human intervention. These AI-driven penetration testing platforms can automatically identify potential attack vectors, chain together multiple vulnerabilities to create complex attack paths, and adapt their strategies based on defensive responses. Machine learning algorithms enable these systems to learn from successful and unsuccessful attack attempts, continuously improving their effectiveness and developing new attack methodologies.
Automated red team systems can simulate advanced persistent threat actors, conducting long-term campaigns that test organizational security awareness, incident response capabilities, and defensive tool effectiveness. These systems provide valuable insights into security posture while reducing the time and resources required for comprehensive security testing, enabling organizations to conduct more frequent and thorough security assessments.
Integration with DevSecOps and Continuous Security
AI-driven vulnerability scanning has become an integral component of DevSecOps practices, enabling continuous security assessment throughout the software development lifecycle. These systems can automatically analyze code commits, assess pull requests for security implications, and provide real-time feedback to developers about potential security issues. The integration of AI security tools with continuous integration and continuous deployment (CI/CD) pipelines ensures that security considerations are embedded throughout the development process rather than being addressed as an afterthought.
The continuous nature of AI-driven security assessment enables organizations to maintain up-to-date security postures in rapidly changing environments. These systems can automatically reassess security posture as new code is deployed, infrastructure changes are implemented, and threat landscapes evolve, providing ongoing security visibility and enabling rapid response to emerging threats.
Advanced Threat Hunting and Incident Response
AI-driven security systems have transformed threat hunting from a manual, intuition-based activity into a data-driven, systematic process supported by machine learning algorithms and automated analysis capabilities. These systems can sift through massive volumes of security logs, network traffic, and system telemetry to identify potential indicators of compromise and suspicious activities that might escape manual analysis. Advanced correlation engines can identify complex attack patterns that span multiple systems, time periods, and attack vectors.
The incident response capabilities of AI-driven security systems enable rapid threat containment and remediation through automated response actions and intelligent alert prioritization. Machine learning algorithms can assess the severity and scope of security incidents, recommend appropriate response actions, and coordinate defensive measures across multiple security tools and platforms.
Compliance Automation and Regulatory Assessment
Regulatory compliance represents a significant challenge for organizations across various industries, requiring continuous monitoring and assessment of security controls, data protection measures, and operational procedures. AI-driven compliance assessment tools can automatically evaluate organizational security postures against regulatory requirements, industry standards, and internal security policies. These systems can identify compliance gaps, recommend remediation actions, and generate comprehensive compliance reports that support audit activities and regulatory submissions.
The automation capabilities of AI-driven compliance tools significantly reduce the time and resources required for compliance management while improving the accuracy and consistency of compliance assessments. Machine learning algorithms can adapt to evolving regulatory requirements and industry best practices, ensuring that compliance assessments remain current and relevant as regulatory landscapes change.

The comparative analysis demonstrates the superior effectiveness of AI-enhanced security scanning across various threat categories. AI-driven systems consistently outperform traditional scanning methods, particularly in detecting sophisticated attacks like zero-day exploits and logic flaws that often evade conventional security tools.
Future Directions and Emerging Technologies
The future of AI-driven security vulnerability scanning promises even more sophisticated capabilities as machine learning technologies continue to evolve and mature. Quantum-resistant security assessment tools are being developed to address the potential threats posed by quantum computing to current cryptographic systems. Advanced AI models are being trained on increasingly diverse and comprehensive datasets, improving their ability to identify novel attack vectors and emerging threat patterns.
The integration of AI with emerging technologies such as blockchain, edge computing, and Internet of Things (IoT) devices is creating new opportunities for comprehensive security assessment across diverse and distributed technology environments. These developments will enable organizations to maintain robust security postures as their technology infrastructures become increasingly complex and interconnected.
The continued advancement of AI-driven security tools will likely lead to more autonomous security systems capable of not only identifying vulnerabilities but also implementing automatic remediation actions and adapting defensive strategies in real-time. This evolution toward autonomous security will enable organizations to respond to threats at machine speed while maintaining human oversight and strategic direction of security operations.
Disclaimer
This article is for informational purposes only and does not constitute professional cybersecurity advice. The views expressed are based on current understanding of AI technologies and their applications in cybersecurity. Organizations should conduct thorough evaluations of AI-driven security tools and consider their specific security requirements, regulatory obligations, and risk tolerances when implementing these technologies. The effectiveness of AI-driven security systems may vary depending on implementation quality, data availability, and organizational security practices.
