The cybersecurity landscape faces an unprecedented challenge as ransomware attacks continue to evolve in sophistication and scale, causing billions of dollars in damages annually and disrupting critical infrastructure worldwide. Traditional signature-based detection methods have proven inadequate against modern ransomware variants that employ advanced evasion techniques, zero-day exploits, and polymorphic code structures. In response to this escalating threat, artificial intelligence and machine learning technologies have emerged as powerful defensive tools, offering revolutionary approaches to ransomware detection that can identify malicious behavior patterns in real-time and prevent attacks before they can encrypt valuable data.
Explore the latest AI security developments to understand how cutting-edge technologies are being deployed to combat evolving cyber threats. The integration of machine learning algorithms into cybersecurity frameworks represents a fundamental shift from reactive to proactive defense strategies, enabling organizations to stay ahead of increasingly sophisticated criminal organizations that leverage automation and artificial intelligence in their attack methodologies.
The Evolution of Ransomware Threats
Modern ransomware attacks have transcended simple file encryption schemes to become complex, multi-stage operations that incorporate reconnaissance phases, lateral movement capabilities, data exfiltration components, and sophisticated social engineering elements. Contemporary ransomware families such as Conti, REvil, and BlackMatter employ advanced techniques including living-off-the-land tactics, fileless malware deployment, and targeted exploitation of specific vulnerabilities within enterprise environments. These evolved threats require equally sophisticated detection mechanisms that can analyze behavioral patterns, network communications, and system modifications in real-time to identify potential ransomware activity before it can complete its malicious objectives.
The economic impact of ransomware attacks has grown exponentially, with average ransom demands reaching millions of dollars and recovery costs often exceeding the initial ransom amount when factoring in business disruption, data recovery efforts, regulatory compliance issues, and reputational damage. This financial reality has driven organizations to invest heavily in advanced detection technologies that can provide early warning capabilities and automated response mechanisms to minimize the potential impact of successful ransomware deployments.
Machine Learning Foundations for Threat Detection
Artificial intelligence-powered ransomware detection systems leverage sophisticated machine learning algorithms that can process vast amounts of system telemetry data, network traffic patterns, and behavioral indicators to identify anomalous activities that may indicate ransomware presence. These systems employ supervised learning techniques trained on extensive datasets of known ransomware samples and benign system activities to develop predictive models capable of distinguishing between legitimate user behavior and malicious ransomware operations with remarkable accuracy rates often exceeding traditional signature-based detection methods.
The foundation of effective AI-driven ransomware detection lies in feature engineering processes that extract meaningful indicators from raw system data, including file system access patterns, registry modifications, network communication behaviors, process creation sequences, and memory allocation patterns. Advanced machine learning models such as random forests, support vector machines, neural networks, and ensemble methods process these features to create comprehensive threat assessment profiles that can adapt to new ransomware variants without requiring manual signature updates or rule modifications.
Enhance your security posture with Claude’s advanced AI capabilities for comprehensive threat analysis and intelligent security decision-making. The combination of natural language processing and machine learning enables sophisticated analysis of threat intelligence feeds, security logs, and incident response data to provide actionable insights for security teams.
Behavioral Analysis and Anomaly Detection
One of the most significant advantages of AI-powered ransomware detection systems lies in their ability to perform sophisticated behavioral analysis that identifies characteristic ransomware activities regardless of the specific malware family or variant being deployed. These systems monitor critical system behaviors such as rapid file modification patterns, unusual encryption activities, suspicious network communications with command-and-control servers, and abnormal privilege escalation attempts that commonly precede ransomware deployment phases.
Machine learning algorithms excel at establishing baseline behavioral patterns for individual systems and user accounts, enabling them to detect deviations that may indicate compromised systems or insider threats attempting to deploy ransomware manually. This behavioral approach proves particularly effective against zero-day ransomware variants that have not yet been catalogued by traditional security vendors, as the underlying behavioral patterns remain consistent across different ransomware families despite variations in specific implementation details.
Advanced anomaly detection algorithms continuously analyze system performance metrics, file access patterns, network traffic volumes, and user behavior indicators to identify subtle changes that may precede ransomware attacks. These systems can detect reconnaissance activities, credential harvesting attempts, and lateral movement behaviors that often occur days or weeks before the actual ransomware payload is deployed, providing security teams with extended time windows for threat containment and remediation activities.
Real-Time Threat Intelligence Integration
Modern AI-powered ransomware detection systems integrate comprehensive threat intelligence feeds that provide real-time information about emerging ransomware campaigns, tactics, techniques, and procedures employed by various criminal organizations. Machine learning algorithms process this intelligence data alongside local system telemetry to create dynamic threat assessment models that can rapidly adapt to new attack methodologies and emerging ransomware families without requiring manual intervention or system updates.
The integration of global threat intelligence enables local detection systems to benefit from collective security knowledge gathered from diverse organizational environments, creating a shared defense capability that improves the overall effectiveness of ransomware detection across entire industry sectors. This collaborative approach allows individual organizations to leverage insights gained from attacks against other entities, significantly reducing the time required to develop effective countermeasures against new ransomware variants.
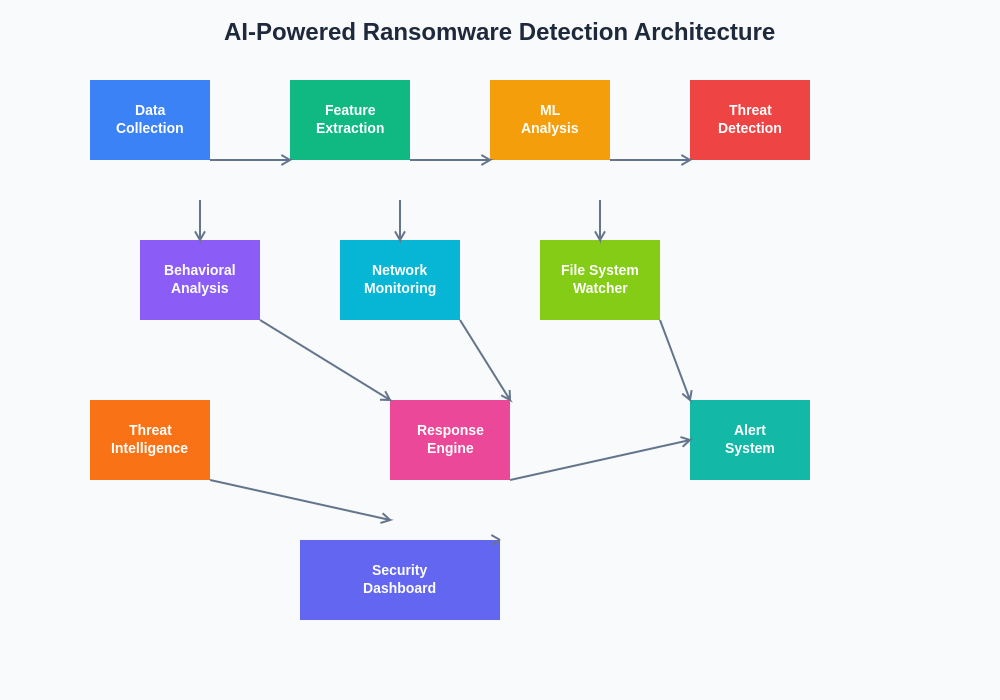
The sophisticated architecture of AI-driven ransomware detection systems incorporates multiple analytical layers that process different types of security data simultaneously, creating comprehensive threat assessment capabilities that far exceed the limitations of traditional signature-based detection methods. This multi-layered approach ensures robust protection against diverse attack vectors while minimizing false positive rates that can overwhelm security teams.
Advanced Feature Engineering for Malware Identification
The effectiveness of machine learning-based ransomware detection systems heavily depends on sophisticated feature engineering processes that extract meaningful indicators from complex system data streams. Advanced feature extraction techniques analyze file entropy levels, API call sequences, memory allocation patterns, network protocol usage, and system resource consumption metrics to create comprehensive behavioral fingerprints that uniquely identify ransomware activities across different system environments and deployment scenarios.
Dynamic feature engineering algorithms continuously evaluate the predictive value of different behavioral indicators, automatically adjusting feature weights and selection criteria based on emerging threat patterns and attack methodologies. This adaptive approach ensures that detection systems remain effective against evolving ransomware tactics while maintaining computational efficiency and minimizing the impact on system performance during normal operations.
Statistical analysis techniques identify correlations between seemingly unrelated system events that may indicate coordinated ransomware deployment activities, such as simultaneous network reconnaissance, credential enumeration, and backup system targeting that commonly precede large-scale ransomware attacks. These correlation analyses enable early detection of multi-stage attacks that might otherwise remain undetected until the final encryption phase begins.
Network Traffic Analysis and Communication Pattern Recognition
AI-powered ransomware detection systems employ sophisticated network traffic analysis capabilities that identify characteristic communication patterns associated with ransomware operations, including command-and-control server communications, data exfiltration activities, and coordination messages between compromised systems within the target network. Machine learning algorithms analyze packet metadata, communication timing patterns, payload characteristics, and destination analysis to identify potential ransomware-related network activities.
Deep packet inspection capabilities enhanced by machine learning algorithms can identify encrypted communications that may indicate ransomware command-and-control activities, even when traditional signature-based systems cannot analyze the encrypted payload contents. These systems analyze communication metadata, timing patterns, and traffic volume characteristics to identify suspicious network behaviors that correlate with known ransomware communication profiles.
Network behavior analysis extends beyond individual system monitoring to encompass comprehensive network-wide visibility that can identify lateral movement activities, privilege escalation attempts, and coordinated multi-system compromise patterns that indicate advanced persistent threat activities commonly associated with targeted ransomware campaigns. This network-centric approach provides security teams with comprehensive situational awareness capabilities that enable effective threat containment and incident response activities.
Leverage Perplexity’s advanced research capabilities to stay informed about emerging ransomware tactics and defensive countermeasures through comprehensive threat intelligence analysis. The combination of AI-powered research tools and machine learning-based detection systems creates a powerful defensive ecosystem that adapts to evolving threat landscapes.
Endpoint Protection and System Hardening
Machine learning-enhanced endpoint protection systems provide comprehensive ransomware defense capabilities that extend beyond traditional antivirus functionality to include behavioral monitoring, application whitelisting, privilege management, and automated incident response capabilities. These integrated systems leverage AI algorithms to make real-time decisions about process execution, file access permissions, and network communications based on comprehensive risk assessments that consider multiple behavioral factors simultaneously.
Advanced endpoint protection platforms employ machine learning models that continuously learn from system activities to establish personalized security baselines for individual devices and user accounts. This personalized approach enables highly accurate detection of anomalous behaviors that may indicate ransomware infections while minimizing false positive alerts that can reduce user productivity and overwhelm security teams with unnecessary incident investigations.
Predictive system hardening capabilities analyze system configurations, installed applications, and user behavior patterns to identify potential vulnerabilities that could be exploited by ransomware attacks. These systems automatically implement appropriate security controls, update system configurations, and recommend additional protective measures based on comprehensive risk assessments that consider both current threat landscapes and historical attack patterns.
Automated Incident Response and Threat Containment
AI-powered ransomware detection systems incorporate sophisticated automated response capabilities that can immediately contain detected threats, isolate affected systems, and initiate recovery procedures without requiring manual intervention from security personnel. These automated response systems leverage machine learning algorithms to assess threat severity, determine appropriate containment strategies, and coordinate response activities across multiple security tools and system components.
Intelligent threat containment algorithms can automatically isolate affected network segments, disable compromised user accounts, terminate suspicious processes, and initiate system recovery procedures based on real-time threat assessments and predefined response protocols. This automated approach significantly reduces the time between threat detection and effective containment, minimizing the potential impact of successful ransomware attacks on critical business operations.
Advanced incident response automation incorporates lessons learned from previous security incidents to continuously improve response effectiveness and reduce mean time to recovery from ransomware attacks. Machine learning algorithms analyze incident response data to identify optimal containment strategies, resource allocation approaches, and recovery procedures that minimize business disruption while ensuring complete threat elimination.
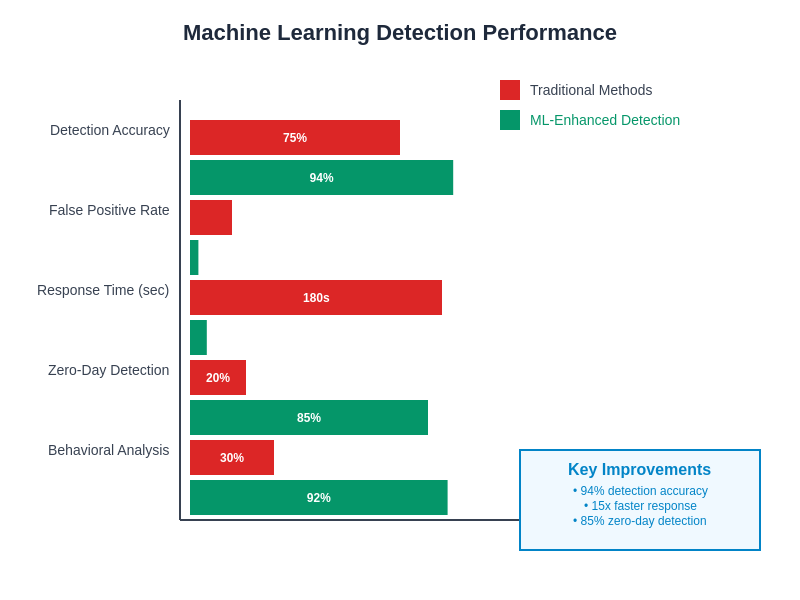
The quantitative performance advantages of machine learning-based ransomware detection systems demonstrate significant improvements in detection accuracy, false positive rates, and response times compared to traditional signature-based approaches. These performance metrics validate the effectiveness of AI-powered security solutions in addressing the evolving ransomware threat landscape.
Cloud-Based Security Analytics and Scalability
Cloud-native AI security platforms provide scalable ransomware detection capabilities that can process massive volumes of security telemetry data from distributed organizational environments while maintaining real-time analysis and response capabilities. These cloud-based systems leverage distributed computing architectures and advanced machine learning algorithms to provide comprehensive threat detection coverage across hybrid cloud environments, remote workforces, and complex multi-site organizational infrastructures.
The scalability advantages of cloud-based AI security platforms enable organizations to implement enterprise-wide ransomware protection without requiring significant investments in local computing infrastructure or specialized security personnel. These platforms automatically scale computational resources based on analysis requirements and threat activity levels, ensuring consistent protection effectiveness regardless of organizational size or complexity.
Global threat intelligence integration capabilities provide cloud-based security platforms with access to comprehensive threat data from diverse organizational environments, enabling rapid identification of new ransomware variants and attack methodologies. This collective intelligence approach significantly improves the effectiveness of individual organizational defenses while contributing to broader cybersecurity community knowledge and threat response capabilities.
Integration with Security Operations Center Workflows
Modern AI-powered ransomware detection systems seamlessly integrate with existing security operations center workflows, providing enriched threat intelligence, automated alert prioritization, and intelligent incident escalation capabilities that enhance the effectiveness of human security analysts. These integrations leverage machine learning algorithms to analyze alert contexts, assess threat severity levels, and provide actionable recommendations that enable security teams to focus their attention on the most critical threats.
Intelligent alert correlation capabilities reduce alert fatigue by consolidating related security events into comprehensive incident reports that provide security analysts with complete situational awareness and recommended response strategies. This consolidation approach significantly improves analyst productivity while ensuring that critical threats receive appropriate attention and resources for effective resolution.
Advanced workflow automation capabilities enable seamless integration between AI-powered detection systems and established incident response procedures, security information and event management platforms, and threat intelligence management systems. These integrations create cohesive security ecosystems that leverage the strengths of both automated analysis capabilities and human expertise to provide comprehensive ransomware protection.
Regulatory Compliance and Data Protection Considerations
AI-powered ransomware detection systems incorporate comprehensive compliance monitoring capabilities that ensure organizational adherence to relevant regulatory requirements while maintaining effective threat protection coverage. These systems automatically generate detailed audit logs, compliance reports, and incident documentation that satisfy regulatory reporting requirements for various industry sectors and geographical jurisdictions.
Data privacy protection mechanisms ensure that AI-powered security systems analyze threat indicators and behavioral patterns without compromising sensitive organizational data or personal information. Advanced privacy-preserving machine learning techniques enable effective threat detection while maintaining strict data confidentiality requirements and regulatory compliance obligations.
Risk assessment capabilities continuously evaluate organizational security postures against relevant regulatory frameworks, industry standards, and best practice recommendations to identify potential compliance gaps and recommend appropriate remediation strategies. This proactive compliance approach helps organizations maintain regulatory adherence while implementing effective ransomware protection measures.
Future Developments in AI-Powered Cybersecurity
The continued evolution of artificial intelligence and machine learning technologies promises even more sophisticated ransomware detection capabilities that will leverage advanced techniques such as federated learning, explainable AI, and quantum-resistant security algorithms. These emerging technologies will enable more effective threat detection while providing greater transparency into AI decision-making processes and enhanced protection against future quantum computing threats.
Integration of advanced natural language processing capabilities will enable AI security systems to analyze unstructured threat intelligence sources, security research publications, and dark web communications to identify emerging ransomware trends and attack methodologies before they become widespread. This predictive threat intelligence capability will provide organizations with advanced warning of new threats and enable proactive defensive preparations.
The development of adversarial machine learning techniques will improve the resilience of AI-powered security systems against attacks specifically designed to evade or compromise machine learning-based detection algorithms. These defensive capabilities will ensure that AI security systems remain effective even as criminal organizations develop their own AI-powered attack tools and evasion techniques.
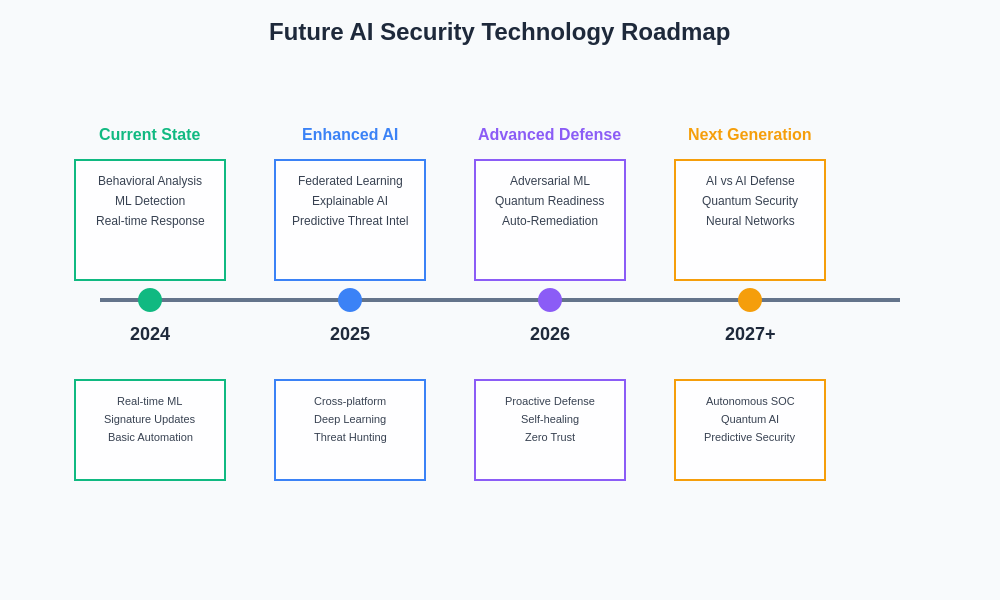
The technological roadmap for AI-powered cybersecurity demonstrates the rapid pace of innovation in defensive technologies and highlights the potential for even more sophisticated threat detection and response capabilities in the near future. Organizations that invest in advanced AI security technologies today will be better positioned to defend against tomorrow’s evolving threat landscape.
Implementation Strategies and Best Practices
Successful implementation of AI-powered ransomware detection systems requires comprehensive planning processes that consider organizational infrastructure requirements, integration complexities, staff training needs, and ongoing maintenance responsibilities. Organizations should develop phased implementation strategies that gradually introduce AI-powered capabilities while maintaining existing security controls and ensuring business continuity throughout the transition process.
Staff training and skill development programs ensure that security teams can effectively leverage AI-powered detection capabilities while maintaining the ability to perform manual analysis and response activities when necessary. These training programs should cover AI system operation, threat analysis methodologies, incident response procedures, and ongoing system optimization techniques that maximize the effectiveness of AI-powered security investments.
Continuous monitoring and optimization processes ensure that AI-powered ransomware detection systems maintain peak effectiveness as threat landscapes evolve and organizational environments change. Regular performance assessments, model retraining activities, and configuration adjustments help organizations maximize their return on AI security investments while maintaining comprehensive protection against emerging ransomware threats.
The integration of artificial intelligence and machine learning technologies into cybersecurity defense strategies represents a fundamental transformation in how organizations approach ransomware threat protection. These advanced technologies provide unprecedented capabilities for early threat detection, automated response, and predictive security analysis that far exceed the limitations of traditional signature-based approaches. As ransomware attacks continue to evolve in sophistication and scale, AI-powered detection systems will become increasingly critical for maintaining effective organizational security postures and protecting valuable digital assets from criminal exploitation.
Disclaimer
This article is for informational purposes only and does not constitute professional cybersecurity advice. The information provided is based on current understanding of AI technologies and their applications in ransomware detection. Organizations should consult with qualified cybersecurity professionals and conduct thorough risk assessments before implementing AI-powered security solutions. The effectiveness of AI-based detection systems may vary depending on specific deployment environments, threat landscapes, and implementation approaches. This content does not endorse any specific security products or vendors.