The exponential growth of artificial intelligence-generated content has created an unprecedented challenge in the digital landscape, necessitating sophisticated methods to protect intellectual property, verify authenticity, and maintain trust in an era where distinguishing between human-created and machine-generated content becomes increasingly difficult. AI watermarking has emerged as a critical defensive technology that embeds imperceptible yet detectable signatures into generated content, providing a robust framework for content protection, ownership verification, and authenticity assurance across diverse digital media formats.
Stay updated with the latest AI security trends to understand emerging threats and protection mechanisms that are shaping the future of digital content security. The development of sophisticated watermarking techniques represents a fundamental shift in how we approach content protection, moving beyond traditional copyright mechanisms to embrace AI-native solutions that can keep pace with rapidly evolving generative technologies.
Understanding AI Watermarking Fundamentals
AI watermarking operates on the principle of embedding invisible yet mathematically detectable patterns directly into the generation process of artificial intelligence models, creating content that carries persistent signatures throughout its lifecycle regardless of subsequent modifications or transformations. Unlike traditional watermarking methods that apply external marks to existing content, AI watermarking integrates protection mechanisms at the source level, ensuring that every piece of generated content inherently contains identifying information that can be reliably extracted and verified using specialized detection algorithms.
This fundamental approach addresses the core challenge of protecting AI-generated content by making watermarking an integral part of the creation process rather than an afterthought. The embedded watermarks remain resilient against common content manipulations such as compression, resizing, format conversion, and minor editing operations, providing persistent protection that maintains effectiveness throughout the content’s distribution and usage lifecycle.
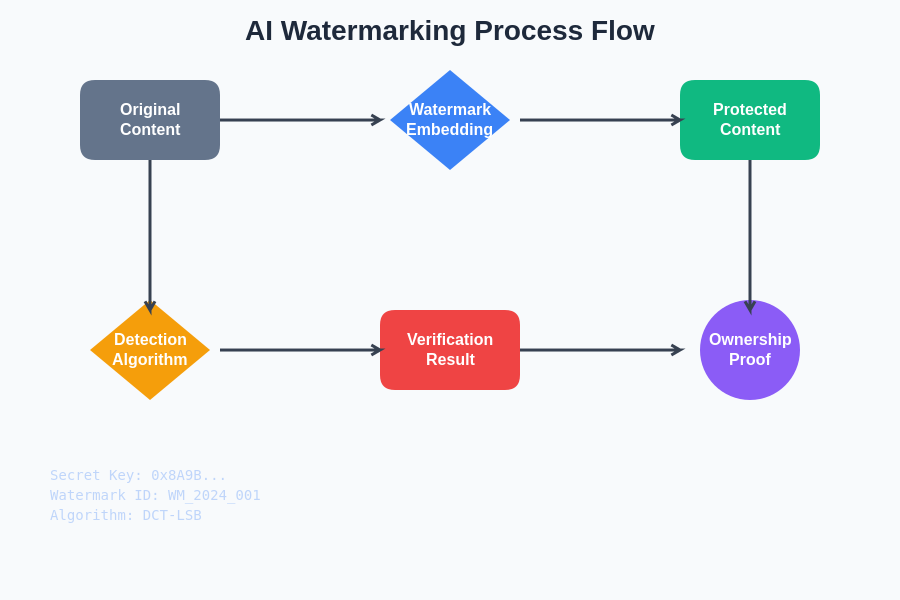
The comprehensive watermarking workflow demonstrates how content protection integrates seamlessly from initial generation through final verification, ensuring that every piece of AI-generated content carries verifiable ownership information while maintaining optimal quality and usability for end users.
The mathematical foundations of AI watermarking rely on sophisticated signal processing techniques that leverage the high-dimensional nature of neural network outputs to embed information in ways that are statistically undetectable to human perception yet computationally recoverable through appropriate detection mechanisms. This approach ensures that watermarked content maintains its original quality and functionality while carrying verifiable ownership and authenticity information.
Technical Implementation Strategies
The implementation of AI watermarking systems requires careful consideration of multiple technical factors including robustness against attacks, computational efficiency, imperceptibility to human users, and compatibility with diverse AI model architectures. Modern watermarking implementations typically employ frequency domain transformations, statistical embedding techniques, or direct neural network modifications that integrate watermarking capabilities into the model’s inference pipeline without significantly impacting performance or output quality.
Enhance your AI projects with Claude’s advanced capabilities for implementing sophisticated watermarking solutions that balance security requirements with practical deployment considerations. The technical complexity of watermarking implementation varies significantly depending on the target content type, required security level, and operational constraints of the deployment environment.
Frequency domain watermarking techniques leverage mathematical transformations such as discrete cosine transforms or wavelet decompositions to embed watermark information in frequency components that are less perceptible to human observers while remaining robust against common content manipulations. These methods work particularly well for image and audio content where frequency domain representations provide natural hiding spaces for watermark data.
Statistical watermarking approaches modify the statistical properties of generated content in subtle ways that can be detected through specialized analysis algorithms. These techniques often involve adjusting probability distributions, correlation patterns, or higher-order statistical moments in ways that preserve content quality while enabling reliable watermark detection.
Neural network-based watermarking integrates protection mechanisms directly into the model architecture, training AI systems to inherently produce watermarked content without requiring separate post-processing steps. This approach offers superior integration and efficiency but requires careful model design and training procedures to ensure watermark reliability and content quality.
Content Type Specific Applications
Different types of AI-generated content require specialized watermarking approaches that account for the unique characteristics and vulnerabilities of each medium. Image watermarking for AI-generated artwork and photographs typically employs spatial domain modifications or frequency domain embedding techniques that preserve visual quality while providing robust detection capabilities. Video content presents additional challenges due to temporal consistency requirements and the need to maintain watermark persistence across frame sequences and video compression operations.
Text watermarking for AI-generated written content involves sophisticated linguistic techniques that modify word choices, sentence structures, or semantic relationships in ways that preserve meaning and readability while embedding detectable patterns. These approaches must carefully balance detectability with natural language flow to avoid creating content that appears artificial or awkward to human readers.
Audio watermarking for AI-generated music, speech, and sound effects requires techniques that operate within the human auditory system’s perceptual limitations while maintaining audio quality and artistic integrity. Psychoacoustic models guide the watermarking process to ensure that embedded information remains inaudible while surviving common audio processing operations such as format conversion, compression, and filtering.
Code and software watermarking presents unique challenges as generated programming code must maintain functional correctness while carrying identifying information. Techniques for code watermarking often involve variable naming patterns, comment structures, or algorithmic choices that preserve functionality while enabling ownership verification.
Advanced Detection Mechanisms
The effectiveness of AI watermarking systems depends critically on the sophistication and reliability of detection mechanisms that can accurately identify watermarked content while minimizing false positive and false negative rates. Modern detection systems employ machine learning algorithms trained specifically to recognize watermark patterns while accounting for various types of content modifications and attacks that might compromise watermark integrity.
Statistical detection methods analyze content characteristics to identify subtle patterns or anomalies that indicate the presence of watermarks. These approaches often use hypothesis testing, correlation analysis, or machine learning classification to distinguish between watermarked and non-watermarked content with high accuracy and reliability.
Deep learning-based detection leverages neural networks trained on large datasets of watermarked and non-watermarked content to develop sophisticated pattern recognition capabilities. These systems can adapt to new watermarking techniques and attack methods through continuous learning while maintaining high detection accuracy across diverse content types and quality levels.
Multi-modal detection systems combine information from multiple sources or content characteristics to improve detection reliability and robustness. By analyzing various aspects of content simultaneously, these systems can achieve higher accuracy and better resistance to sophisticated attacks designed to evade single-mode detection methods.
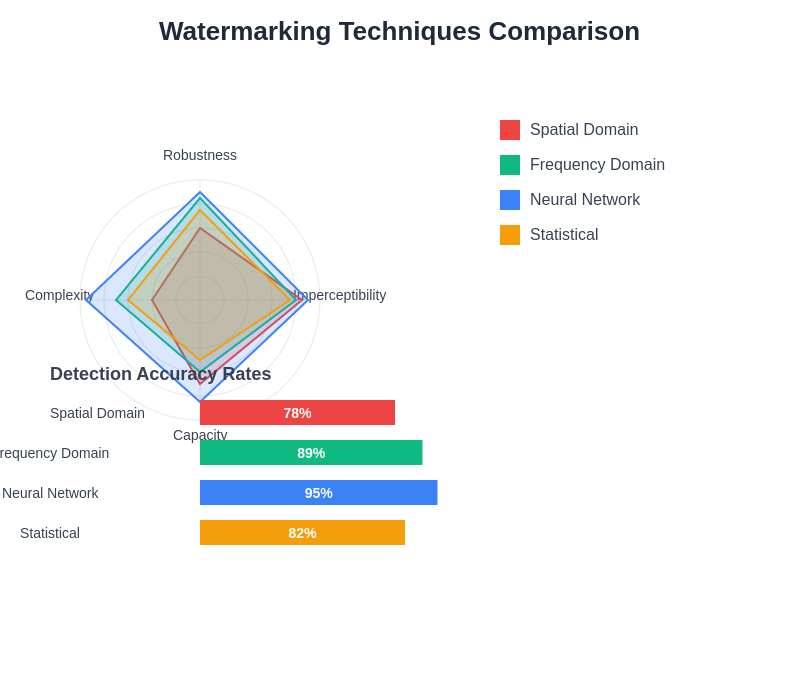
The comparative analysis of different watermarking techniques reveals significant variations in performance characteristics, with neural network-based approaches demonstrating superior robustness and imperceptibility while requiring higher computational complexity for implementation and deployment.
Robustness Against Adversarial Attacks
The security of AI watermarking systems faces constant challenges from adversarial attacks designed to remove, modify, or forge watermarks while preserving content usability. Understanding and defending against these attacks represents a critical aspect of watermarking system design that requires ongoing research and development to maintain effectiveness against evolving threats.
Explore comprehensive AI research capabilities with Perplexity to stay informed about emerging attack vectors and defensive strategies in the rapidly evolving field of AI content protection. The adversarial landscape for watermarking includes both passive attacks that attempt to remove watermarks without detection and active attacks that try to forge or manipulate watermark information.
Geometric attacks involve transformations such as rotation, scaling, cropping, or perspective changes that aim to disrupt watermark integrity while preserving content visual appearance. Robust watermarking systems must account for these transformations through invariant embedding techniques or normalization procedures that maintain detectability despite geometric modifications.
Statistical attacks attempt to remove watermarks through noise addition, filtering, compression, or other signal processing operations that degrade watermark signal strength while minimizing impact on content quality. Defense against these attacks requires watermarking techniques that embed information in robust signal components that resist statistical manipulation.
Protocol attacks target the watermarking system’s operational procedures rather than the embedded watermarks themselves, attempting to exploit vulnerabilities in key management, detection processes, or verification protocols. Comprehensive security requires addressing these system-level vulnerabilities through proper cryptographic design and secure implementation practices.
Industry Standards and Compliance
The development of AI watermarking technologies has prompted efforts to establish industry standards and compliance frameworks that ensure interoperability, security, and effectiveness across different implementations and use cases. These standards address technical specifications, security requirements, performance benchmarks, and evaluation methodologies that guide the development and deployment of watermarking solutions.
International standardization organizations are working to develop comprehensive frameworks for AI content protection that encompass watermarking technologies, detection protocols, and verification procedures. These efforts aim to create unified approaches that support global content protection while accommodating diverse regional requirements and regulatory frameworks.
Compliance considerations for AI watermarking include privacy protection requirements, data sovereignty regulations, and intellectual property laws that vary across jurisdictions and industries. Organizations implementing watermarking solutions must navigate these complex regulatory landscapes while maintaining technical effectiveness and operational efficiency.
Industry-specific standards address unique requirements for different sectors such as media and entertainment, healthcare, financial services, and government applications. These specialized frameworks account for sector-specific security requirements, performance constraints, and regulatory compliance needs that influence watermarking system design and implementation.
Implementation Challenges and Solutions
Practical deployment of AI watermarking systems faces numerous technical and operational challenges that require careful consideration and innovative solutions. Computational overhead represents a significant concern as watermarking processes must integrate seamlessly into existing AI workflows without substantially impacting generation speed or resource utilization.
Scalability challenges arise when watermarking systems must handle large volumes of content generation while maintaining consistent protection quality and detection reliability. Cloud-based implementations and distributed processing architectures provide potential solutions but introduce additional complexity in key management and security coordination.
Quality preservation remains a critical challenge as watermarking techniques must embed sufficient information for reliable detection while maintaining the aesthetic, functional, or perceptual quality that makes generated content valuable. Advanced optimization techniques and perceptual quality metrics guide the development of watermarking methods that achieve optimal trade-offs between protection strength and content quality.
Integration complexity emerges when incorporating watermarking capabilities into existing AI development workflows, deployment pipelines, and content management systems. Successful implementations require careful planning, comprehensive testing, and gradual rollout strategies that minimize disruption while ensuring adequate protection coverage.
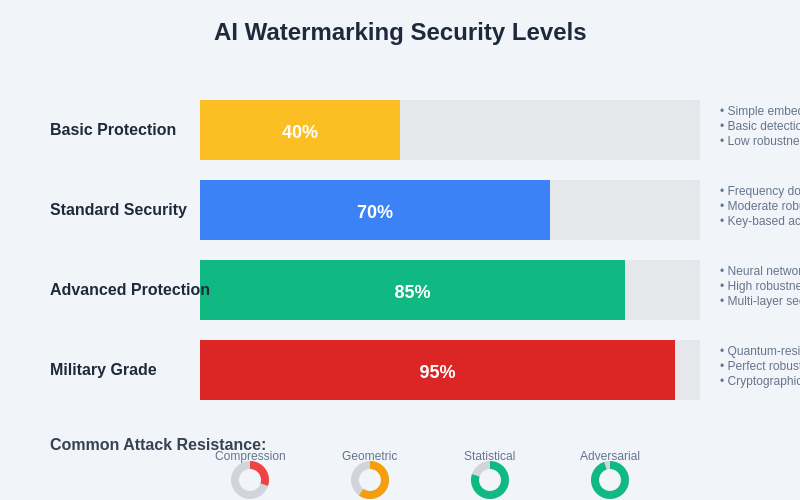
The graduated security framework for AI watermarking systems provides organizations with flexible implementation options that balance protection requirements with operational constraints, enabling appropriate security measures for different risk profiles and use cases.
Performance Optimization Strategies
Optimizing AI watermarking performance requires balancing multiple competing objectives including detection accuracy, computational efficiency, content quality preservation, and robustness against attacks. Modern optimization approaches employ advanced mathematical techniques, machine learning algorithms, and system-level optimizations to achieve superior performance across these dimensions.
Algorithmic optimization focuses on developing more efficient embedding and detection algorithms that achieve superior performance with reduced computational requirements. These improvements often involve mathematical innovations, better signal processing techniques, or more effective machine learning model architectures that optimize the fundamental watermarking operations.
System-level optimization addresses infrastructure considerations such as hardware acceleration, parallel processing, caching strategies, and distributed computing approaches that improve overall watermarking system performance. Graphics processing units, specialized AI accelerators, and cloud computing resources provide opportunities for significant performance improvements in large-scale deployments.
Adaptive optimization techniques dynamically adjust watermarking parameters based on content characteristics, security requirements, or performance constraints to achieve optimal results for specific use cases. These approaches use machine learning, feedback mechanisms, or real-time analysis to continuously optimize watermarking performance while maintaining security and quality requirements.
Legal and Ethical Considerations
The deployment of AI watermarking technologies raises important legal and ethical questions regarding privacy rights, content ownership, surveillance capabilities, and the potential for misuse in restricting legitimate content usage. These considerations require careful balance between protection benefits and potential negative impacts on digital rights and freedoms.
Privacy implications arise when watermarking systems collect, store, or transmit information about content creators, users, or usage patterns. Responsible implementations must address these concerns through privacy-preserving techniques, data minimization practices, and transparent disclosure of data collection and usage policies.
Ownership and attribution challenges emerge when watermarking technologies are used to establish or verify content ownership in legal disputes or commercial transactions. The legal framework for watermark-based ownership claims continues to evolve as courts and regulatory bodies develop precedents for evaluating watermark evidence.
Censorship and control concerns relate to the potential use of watermarking technologies to track, restrict, or control content distribution in ways that may infringe upon free expression rights. Balancing legitimate protection needs with preservation of digital rights requires careful consideration of implementation approaches and usage policies.
Future Developments and Innovations
The field of AI watermarking continues to evolve rapidly as researchers and developers work to address emerging challenges and opportunities in content protection. Advances in quantum computing, advanced cryptography, and next-generation AI architectures promise to enable new watermarking capabilities while potentially threatening the security of existing approaches.
Quantum-resistant watermarking represents an emerging area of research as quantum computing developments may compromise current cryptographic foundations of watermarking systems. Developing protection mechanisms that remain secure against quantum attacks requires fundamental advances in mathematical techniques and system architectures.
Blockchain integration offers potential benefits for watermarking systems through decentralized verification, immutable audit trails, and distributed key management capabilities. These technologies may enable more robust and transparent content protection frameworks that reduce reliance on centralized authorities while improving security and accountability.
Cross-modal watermarking explores techniques that can embed and detect watermarks across different content types and formats, enabling more comprehensive protection for complex digital assets that may include multiple media types or undergo format transformations during distribution and usage.
The integration of AI watermarking with broader content security ecosystems promises to create comprehensive protection frameworks that address multiple aspects of digital content security including authentication, integrity verification, access control, and usage monitoring. These integrated approaches may provide more effective and user-friendly solutions for protecting valuable digital assets in increasingly complex technological environments.
Disclaimer
This article is for informational purposes only and does not constitute legal, technical, or professional advice. The information presented reflects current understanding of AI watermarking technologies and their applications, which continue to evolve rapidly. Readers should consult with qualified professionals and conduct thorough research before implementing watermarking solutions or making decisions based on this content. The effectiveness and legality of watermarking approaches may vary significantly depending on specific use cases, jurisdictions, and technical requirements.
