The convergence of artificial intelligence and data privacy has created one of the most significant challenges in modern computing, where organizations must balance the tremendous potential of AI-driven insights with the fundamental requirement to protect sensitive information. Homomorphic encryption emerges as a revolutionary cryptographic technique that addresses this critical challenge by enabling computations to be performed directly on encrypted data without ever decrypting it, fundamentally transforming how we approach privacy-preserving artificial intelligence and machine learning applications.
Explore the latest developments in AI security to understand the cutting-edge innovations that are reshaping data protection in machine learning environments. This groundbreaking approach to secure computation represents a paradigm shift that allows organizations to harness the power of AI while maintaining the highest standards of data confidentiality and regulatory compliance.
Understanding Homomorphic Encryption Fundamentals
Homomorphic encryption represents a sophisticated cryptographic system that possesses the remarkable property of allowing computations to be performed on encrypted data without requiring access to the underlying plaintext information. This mathematical innovation enables the execution of arbitrary functions on encrypted inputs, producing encrypted results that, when decrypted, yield the same outcome as if the operations had been performed on the original unencrypted data. The fundamental principle underlying homomorphic encryption lies in its ability to preserve the algebraic structure of data through the encryption process, ensuring that mathematical relationships and computational operations remain intact even when applied to encrypted information.
The theoretical foundations of homomorphic encryption can be traced back to the early work of Rivest, Adleman, and Dertouzos in 1978, who first conceptualized the possibility of computing on encrypted data. However, it was not until 2009 that Craig Gentry presented the first fully homomorphic encryption scheme in his groundbreaking doctoral thesis, demonstrating that it was indeed possible to perform unlimited computations on encrypted data. This breakthrough opened new possibilities for secure cloud computing, privacy-preserving data analysis, and confidential artificial intelligence applications that were previously considered impossible or impractical.
The mathematical elegance of homomorphic encryption lies in its ability to maintain homomorphic properties across different types of operations. Additive homomorphic schemes allow for the computation of encrypted sums, multiplicative schemes enable encrypted multiplications, and fully homomorphic encryption systems support both addition and multiplication operations, thereby enabling the evaluation of arbitrary polynomial functions on encrypted data. This computational flexibility forms the foundation for implementing complex machine learning algorithms while preserving data confidentiality throughout the entire process.
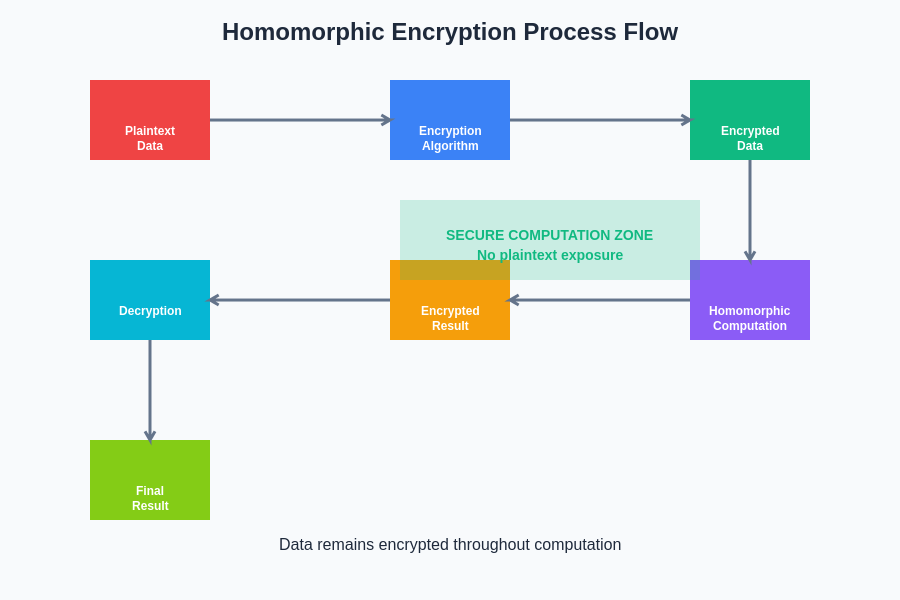
The homomorphic encryption workflow demonstrates how data maintains its privacy throughout the entire computational process. This systematic approach ensures that sensitive information never exists in plaintext form within untrusted computing environments, providing unprecedented security guarantees for AI applications.
Architectural Components and Implementation Models
The implementation of homomorphic encryption systems requires careful consideration of multiple architectural components that work together to enable secure computation on encrypted data. The key generation process involves creating public and private key pairs with specific mathematical properties that support homomorphic operations, while ensuring that the encryption scheme maintains both security and computational efficiency. The encryption mechanism transforms plaintext data into ciphertext format while preserving the algebraic structure necessary for meaningful computations, and the evaluation component performs operations directly on encrypted data without compromising security.
Modern homomorphic encryption implementations typically employ lattice-based cryptographic constructions that leverage the mathematical complexity of problems such as the Learning With Errors problem to provide security guarantees. These schemes incorporate sophisticated noise management techniques to control the accumulation of cryptographic noise that occurs during homomorphic operations, ensuring that computed results remain decryptable and accurate. The bootstrapping process, a crucial innovation in fully homomorphic encryption, enables the refreshing of ciphertexts to reduce noise levels and support unlimited depth computations.
Experience advanced AI capabilities with Claude to explore how sophisticated reasoning systems can be enhanced with privacy-preserving technologies. The integration of homomorphic encryption with AI systems requires careful architectural design to balance computational efficiency, security requirements, and practical implementation constraints while maintaining the performance characteristics necessary for real-world applications.
Applications in Machine Learning and AI
The application of homomorphic encryption to machine learning and artificial intelligence systems opens up unprecedented opportunities for privacy-preserving data analysis and collaborative learning scenarios. In supervised learning applications, homomorphic encryption enables the training of machine learning models on encrypted datasets without revealing sensitive information to the model training infrastructure. This capability is particularly valuable in scenarios involving medical data, financial information, or other sensitive datasets where privacy regulations and confidentiality requirements prohibit traditional data sharing approaches.
Neural network implementations using homomorphic encryption have demonstrated the feasibility of performing forward propagation and inference operations on encrypted data, enabling the deployment of AI models that can process sensitive inputs while maintaining complete data confidentiality. The evaluation of encrypted neural networks involves performing matrix multiplications, activation functions, and other mathematical operations directly on ciphertext, producing encrypted predictions that can be decrypted only by authorized parties. This approach enables organizations to leverage powerful AI models without exposing their sensitive data to third-party service providers or cloud computing platforms.
Federated learning scenarios benefit significantly from homomorphic encryption by enabling secure aggregation of model updates from multiple parties without revealing individual contributions. Participants can encrypt their local model parameters and gradients, allowing for collaborative model training while maintaining the privacy of individual datasets and model components. This approach facilitates the development of robust machine learning models that benefit from diverse datasets while respecting privacy constraints and regulatory requirements across different organizations and jurisdictions.
Performance Optimization and Computational Efficiency
The practical deployment of homomorphic encryption in AI applications requires sophisticated optimization strategies to address the computational overhead associated with encrypted operations. Traditional homomorphic encryption schemes can be orders of magnitude slower than their plaintext counterparts, necessitating careful algorithm design and implementation optimizations to achieve acceptable performance levels. Researchers and practitioners have developed various techniques to improve computational efficiency, including approximate arithmetic schemes, packed ciphertext methods, and specialized hardware acceleration approaches.
Approximate homomorphic encryption schemes, such as the CKKS scheme, enable efficient computation on encrypted real numbers by accepting controlled amounts of precision loss in exchange for significant performance improvements. This trade-off is often acceptable in machine learning applications where approximate computations are inherently part of the optimization process. Packed ciphertext techniques allow multiple values to be encrypted within a single ciphertext, enabling SIMD-style parallel operations that dramatically improve throughput for vector and matrix operations commonly found in AI algorithms.
Hardware acceleration through specialized processors, including GPUs and custom ASICs, has shown promising results in accelerating homomorphic encryption operations. These implementations leverage the parallel nature of cryptographic computations to achieve significant speedups compared to traditional CPU-based approaches. Additionally, algorithmic optimizations such as batching, precomputation techniques, and efficient polynomial arithmetic implementations contribute to making homomorphic encryption more practical for real-world AI applications.
Security Guarantees and Threat Models
The security properties of homomorphic encryption systems provide strong theoretical guarantees against various threat models, making them suitable for deployment in security-critical AI applications. The semantic security property ensures that encrypted data reveals no information about the underlying plaintext, even when an adversary has access to multiple ciphertexts and computational results. This protection extends to scenarios where attackers may have significant computational resources or access to quantum computing capabilities, depending on the specific cryptographic assumptions underlying the encryption scheme.
The threat model for homomorphic encryption in AI applications encompasses various attack scenarios, including honest-but-curious cloud providers, malicious adversaries attempting to extract sensitive information from encrypted computations, and side-channel attacks targeting implementation weaknesses. Modern homomorphic encryption schemes are designed to resist these attacks through careful mathematical construction and implementation practices that minimize information leakage through timing, power consumption, or other observable characteristics.
Enhance your research capabilities with Perplexity to stay informed about the latest security research and threat intelligence related to encrypted computing systems. The formal security analysis of homomorphic encryption schemes involves proving security under well-established cryptographic assumptions, providing confidence in the protection offered by these systems when properly implemented and deployed.
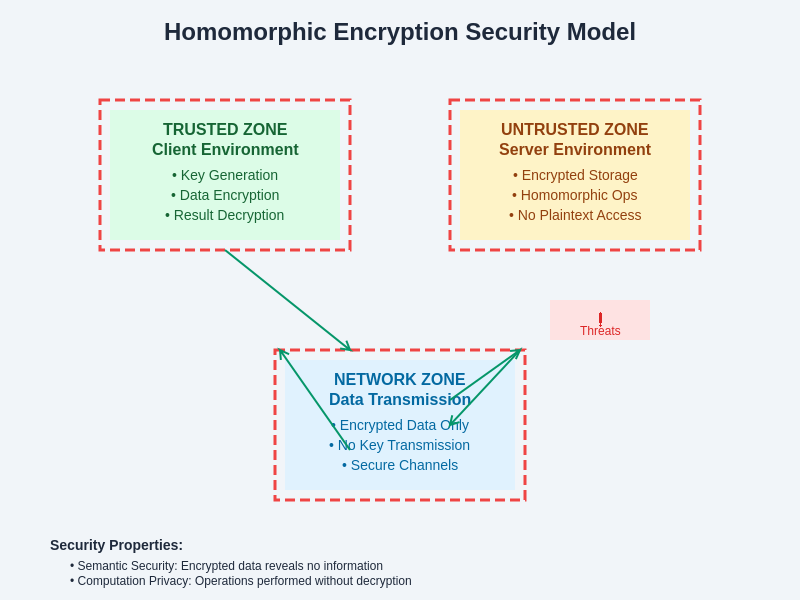
The security architecture of homomorphic encryption systems establishes clear trust boundaries between different computational environments. This model enables secure collaboration across organizational boundaries while maintaining strict data privacy controls and regulatory compliance requirements.
Implementation Challenges and Practical Considerations
The deployment of homomorphic encryption in production AI systems presents numerous implementation challenges that must be carefully addressed to ensure both security and functionality. Key management complexity arises from the need to securely generate, distribute, and maintain cryptographic keys across multiple parties and computational environments. The bootstrapping process, while theoretically elegant, introduces significant computational overhead that can impact system performance and scalability in practical applications.
Parameter selection for homomorphic encryption schemes requires careful balancing of security requirements, computational efficiency, and noise management considerations. Incorrectly chosen parameters can result in either inadequate security protection or excessive computational overhead that renders the system impractical for real-world use. Additionally, the implementation of homomorphic encryption libraries requires expertise in both cryptographic theory and high-performance computing to achieve acceptable performance levels while maintaining security guarantees.
Integration with existing AI frameworks and development tools presents additional challenges, as most machine learning libraries are designed for plaintext operations and must be adapted to work with encrypted data structures. This adaptation process involves not only modifying computational routines but also developing new debugging, monitoring, and optimization tools that can work effectively with encrypted systems. The complexity of these integration challenges often requires specialized expertise and careful system design to achieve successful deployments.
Industry Applications and Use Cases
Healthcare organizations represent one of the most promising application domains for homomorphic encryption in AI, where the ability to perform machine learning on encrypted medical data enables breakthrough research while maintaining strict patient privacy protections. Medical institutions can collaborate on large-scale studies involving sensitive health information without violating HIPAA regulations or other privacy requirements. Pharmaceutical companies can leverage encrypted clinical trial data to develop new treatments and drug discovery algorithms while protecting participant confidentiality and maintaining competitive advantages.
Financial services applications of homomorphic encryption enable secure fraud detection, credit scoring, and risk assessment algorithms that operate on encrypted financial data. Banks and financial institutions can collaborate on anti-money laundering initiatives and fraud prevention systems without sharing sensitive customer information or proprietary detection algorithms. Investment firms can perform encrypted portfolio optimization and algorithmic trading strategies while protecting their proprietary models and client data from competitors and potential attackers.
Government and defense applications leverage homomorphic encryption to enable secure intelligence analysis, encrypted communications processing, and classified data analysis systems. These applications allow multiple agencies to collaborate on sensitive investigations and threat analysis while maintaining appropriate security clearances and information compartmentalization. The ability to perform complex analytical computations on encrypted classified data enables more effective intelligence gathering and analysis while preserving national security requirements.
Emerging Technologies and Future Developments
The evolution of homomorphic encryption continues to accelerate through ongoing research in advanced cryptographic techniques, specialized hardware implementations, and novel algorithmic approaches. Quantum-resistant homomorphic encryption schemes are being developed to address the potential threat posed by quantum computing to current cryptographic systems. These next-generation schemes incorporate post-quantum cryptographic primitives to ensure long-term security even in the presence of powerful quantum adversaries.
Multi-party computation protocols are being integrated with homomorphic encryption to enable even more sophisticated privacy-preserving scenarios where multiple parties can jointly compute functions on their encrypted inputs without revealing individual contributions. These hybrid approaches combine the strengths of different cryptographic techniques to achieve better performance and security characteristics than either approach alone. The development of threshold homomorphic encryption schemes enables distributed decryption processes that eliminate single points of failure and improve system resilience.
Cloud computing platforms are beginning to integrate homomorphic encryption capabilities directly into their infrastructure, providing developers with easy-to-use APIs and services for encrypted computation. Major technology companies are investing heavily in homomorphic encryption research and development, recognizing its potential to unlock new business models and applications that were previously impossible due to privacy constraints. These platform-level integrations are expected to significantly accelerate the adoption of homomorphic encryption in mainstream applications.
Standards and Regulatory Landscape
The standardization of homomorphic encryption technologies is progressing through various international standards organizations and industry consortiums. The ISO/IEC working groups are developing comprehensive standards for homomorphic encryption schemes, implementation guidelines, and security evaluation criteria. These standards efforts aim to provide clear guidance for developers and organizations seeking to implement homomorphic encryption systems while ensuring interoperability and security best practices.
Regulatory frameworks for privacy-preserving AI technologies are evolving to address the unique challenges and opportunities presented by homomorphic encryption. GDPR compliance can be enhanced through homomorphic encryption implementations that enable data processing while maintaining the privacy rights of data subjects. Regulatory bodies are developing guidance documents and compliance frameworks that recognize the privacy benefits of encrypted computation while establishing appropriate oversight and audit requirements.
Professional certification programs and training initiatives are being developed to address the skills gap in homomorphic encryption implementation and deployment. Universities and professional organizations are creating specialized curricula and certification programs to train the next generation of cryptographic engineers and privacy-preserving AI specialists. These educational initiatives are crucial for building the workforce necessary to support widespread adoption of homomorphic encryption technologies.
Performance Benchmarks and Practical Limitations
Current performance benchmarks for homomorphic encryption in AI applications demonstrate both the significant potential and the remaining challenges in this field. Simple linear operations such as encrypted matrix multiplications can achieve performance within one to two orders of magnitude of plaintext operations using optimized implementations and specialized hardware. However, complex nonlinear operations and deep neural network evaluations still incur substantial computational overhead that may limit their applicability in time-sensitive applications.
Memory consumption represents another significant practical limitation, as homomorphic ciphertexts are typically much larger than their plaintext counterparts. This expansion factor can range from several times to several orders of magnitude, depending on the specific encryption scheme and security parameters. The increased memory requirements impact not only storage costs but also bandwidth requirements for distributed computing scenarios and cache efficiency in high-performance computing environments.
Precision management in approximate homomorphic encryption schemes introduces additional complexity in AI applications where numerical stability and accuracy are critical. The accumulation of approximation errors during complex computations can impact model accuracy and training convergence, requiring careful algorithm design and error analysis. Practitioners must balance computational efficiency gains from approximate schemes against potential impacts on model performance and reliability.
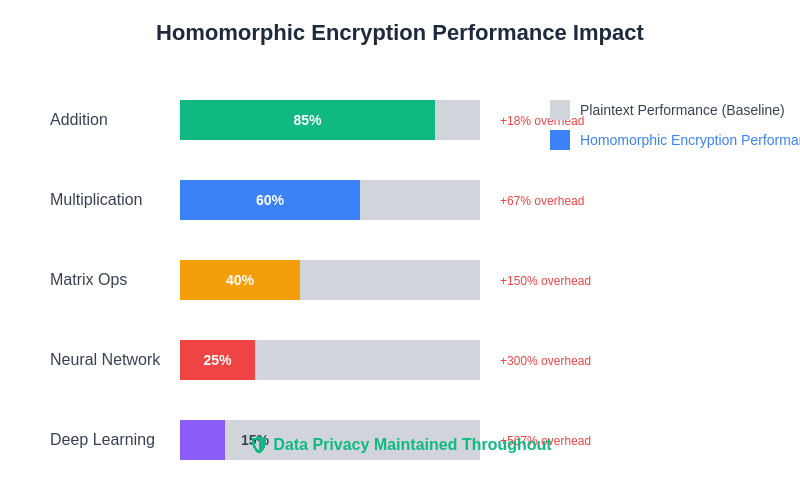
The performance characteristics of homomorphic encryption across different computational operations reveal the trade-offs between security and efficiency. While the overhead is significant, ongoing optimizations continue to narrow the performance gap, making encrypted computation increasingly viable for real-world applications.
Integration with Existing AI Ecosystems
The integration of homomorphic encryption with popular machine learning frameworks requires careful consideration of API design, performance optimization, and developer experience. Leading frameworks such as TensorFlow, PyTorch, and scikit-learn are being extended with homomorphic encryption backends that enable seamless transitions from plaintext to encrypted computations. These integrations aim to minimize changes to existing machine learning workflows while providing the security benefits of encrypted computation.
Development tools and debugging environments for homomorphic encryption present unique challenges, as traditional debugging techniques cannot be directly applied to encrypted computations. Specialized profiling tools, encrypted data visualization techniques, and statistical analysis methods are being developed to help developers optimize and troubleshoot homomorphic encryption implementations. These tools are essential for making homomorphic encryption accessible to mainstream AI developers who may not have deep cryptographic expertise.
Deployment and operations considerations for homomorphic encryption in production AI systems include monitoring, logging, and performance optimization in encrypted environments. DevOps practices must be adapted to handle the unique requirements of encrypted computation systems, including key management, performance monitoring, and capacity planning. The development of specialized deployment tools and best practices is crucial for successful production implementations of homomorphic encryption in AI applications.
Economic Impact and Business Models
The economic implications of homomorphic encryption adoption extend far beyond the direct costs of implementation, encompassing new business models, competitive advantages, and market opportunities. Organizations investing in homomorphic encryption capabilities can offer privacy-preserving AI services that differentiate them from competitors and enable access to previously unavailable data sources. This technological advantage can translate into significant revenue opportunities and market positioning benefits in privacy-conscious industries.
Cost-benefit analyses of homomorphic encryption implementations must consider both the direct costs of computational overhead and the indirect benefits of enhanced privacy protection, regulatory compliance, and expanded market access. The total cost of ownership includes not only computational resources but also development costs, specialized expertise requirements, and ongoing maintenance and optimization efforts. However, the value proposition often extends beyond cost considerations to include strategic advantages and risk mitigation benefits.
New privacy-preserving business models enabled by homomorphic encryption include secure data marketplaces, collaborative AI services, and privacy-preserving analytics platforms. These models allow organizations to monetize their data assets while maintaining privacy protections and regulatory compliance. The emergence of these new business models is expected to drive further investment and innovation in homomorphic encryption technologies and applications.
Conclusion and Future Outlook
Homomorphic encryption represents a transformative technology that addresses one of the most fundamental challenges in modern AI applications by enabling secure computation on encrypted data. While current implementations face performance and complexity challenges, ongoing research and development efforts continue to improve the practical feasibility of homomorphic encryption for real-world AI applications. The convergence of advancing cryptographic techniques, specialized hardware acceleration, and growing demand for privacy-preserving AI solutions creates a compelling case for continued investment and development in this field.
The future of homomorphic encryption in AI applications appears increasingly promising as technological barriers continue to diminish and practical implementations become more accessible. Organizations that invest early in developing homomorphic encryption capabilities are likely to gain significant competitive advantages in privacy-sensitive markets and applications. The continued evolution of standards, tools, and best practices will further accelerate adoption and enable new classes of applications that were previously impossible.
The broader implications of widespread homomorphic encryption adoption extend beyond individual organizations to encompass fundamental changes in how society approaches data privacy, collaborative computation, and AI governance. As these technologies mature and become more accessible, they have the potential to reshape the landscape of digital privacy and enable new forms of secure collaboration that balance innovation with privacy protection. The successful deployment of homomorphic encryption in AI applications represents not just a technological achievement but a significant step toward a more privacy-preserving and secure digital future.
Disclaimer
This article is for informational purposes only and does not constitute professional advice regarding cryptographic implementations or security practices. The views expressed are based on current understanding of homomorphic encryption technologies and their applications in artificial intelligence. Readers should conduct thorough research and consult with qualified cryptographic experts before implementing homomorphic encryption systems in production environments. The effectiveness and security of homomorphic encryption implementations depend on proper design, implementation, and deployment practices that require specialized expertise.