The convergence of quantum computing and artificial intelligence represents one of the most profound technological shifts in modern history, fundamentally challenging our understanding of computational security and cryptographic protection. As we stand at the precipice of the quantum era, the traditional cryptographic methods that have safeguarded digital communications for decades face unprecedented threats from quantum-powered algorithms and AI systems capable of breaking conventional encryption schemes with unprecedented efficiency.
Discover the latest developments in AI and quantum computing to understand how these revolutionary technologies are reshaping the landscape of digital security and privacy protection. The implications of this technological convergence extend far beyond academic research, threatening to disrupt financial systems, government communications, healthcare records, and virtually every aspect of our digitally connected world that relies on cryptographic security.
The Quantum Threat to Traditional Cryptography
The emergence of quantum computing capabilities poses an existential threat to the cryptographic foundations upon which modern digital security is built. Traditional public-key cryptographic systems, including RSA, Elliptic Curve Cryptography, and Diffie-Hellman key exchange protocols, derive their security from mathematical problems that are computationally intractable for classical computers but become trivially solvable using quantum algorithms such as Shor’s algorithm.
This vulnerability extends beyond theoretical concerns, as advancing quantum hardware capabilities and the integration of artificial intelligence in quantum system optimization are accelerating the timeline for practical quantum cryptanalysis. The combination of quantum computing power with AI-driven optimization algorithms creates a synergistic effect that could render current cryptographic protections obsolete much sooner than previously anticipated, necessitating immediate and comprehensive preparation for the post-quantum cryptographic transition.
The scale of this challenge cannot be overstated, as virtually every aspect of modern digital infrastructure relies on cryptographic systems that will become vulnerable to quantum attacks. From secure communications and financial transactions to cloud storage encryption and digital identity verification, the entire ecosystem of digital security must be reimagined and reconstructed using quantum-resistant cryptographic methods.
Understanding Post-Quantum Cryptographic Approaches
Post-quantum cryptography encompasses a diverse array of mathematical approaches designed to withstand attacks from both classical and quantum computers, including those enhanced by artificial intelligence systems. These cryptographic methods are based on mathematical problems that are believed to remain computationally difficult even for quantum computers, providing a foundation for securing digital communications in the quantum era.
The primary categories of post-quantum cryptographic approaches include lattice-based cryptography, which relies on the difficulty of finding short vectors in high-dimensional lattices, hash-based signatures that derive security from the one-way properties of cryptographic hash functions, code-based cryptography utilizing error-correcting codes, multivariate cryptography based on solving systems of multivariate polynomial equations, and isogeny-based cryptography leveraging the complexity of finding isogenies between supersingular elliptic curves.
Each approach offers distinct advantages and challenges in terms of security assumptions, performance characteristics, key sizes, and implementation complexity. The selection and optimization of these cryptographic methods must consider not only their resistance to quantum attacks but also their vulnerability to AI-enhanced cryptanalysis techniques that could exploit subtle patterns or weaknesses in their mathematical foundations.
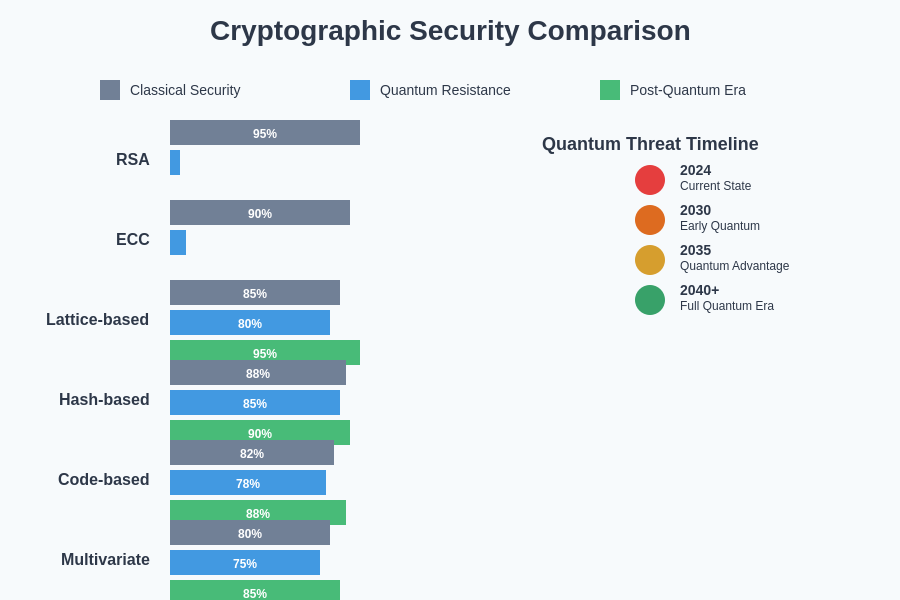
The comparative analysis of different cryptographic approaches reveals significant variations in their effectiveness against classical computers, early quantum systems, and mature quantum-AI hybrid attacks. Understanding these security profiles is crucial for making informed decisions about cryptographic transitions and hybrid security implementations.
Experience advanced AI security analysis with Claude to explore how artificial intelligence can be leveraged both as a tool for enhancing cryptographic security and as a potential vector for sophisticated attacks against post-quantum systems. The dual nature of AI in cryptographic applications requires careful consideration of both defensive and offensive capabilities in designing robust security systems.
AI-Enhanced Quantum Cryptanalysis
The integration of artificial intelligence with quantum computing capabilities represents a paradigm shift in cryptanalytic potential, creating hybrid systems that combine the raw computational power of quantum algorithms with the pattern recognition, optimization, and adaptive learning capabilities of advanced AI systems. This convergence enables unprecedented approaches to breaking cryptographic systems that may prove effective even against some post-quantum cryptographic methods.
Machine learning algorithms can optimize quantum circuit designs for specific cryptanalytic tasks, potentially reducing the quantum resources required to break cryptographic systems and accelerating the practical timeline for quantum attacks. Neural networks trained on cryptographic data patterns may identify previously unknown vulnerabilities or attack vectors in both classical and post-quantum cryptographic systems, while reinforcement learning agents could develop novel attack strategies that evolve and adapt in response to defensive countermeasures.
The implications extend to side-channel attacks, where AI systems could analyze power consumption, electromagnetic emissions, timing variations, and other physical characteristics of cryptographic implementations to extract secret keys or other sensitive information. The combination of quantum sensing capabilities with AI-driven signal processing could enable unprecedented precision in side-channel analysis, potentially compromising even quantum-resistant cryptographic systems through implementation vulnerabilities.
Quantum-Safe AI System Architecture
The development of artificial intelligence systems that remain secure and functional in a post-quantum world requires fundamental reconsideration of AI architecture, data protection methods, and communication protocols. Traditional approaches to securing AI systems rely heavily on cryptographic methods that will become vulnerable to quantum attacks, necessitating comprehensive redesign of AI security frameworks using post-quantum cryptographic primitives.
This transformation encompasses secure model training environments where sensitive training data and proprietary algorithms are protected using quantum-resistant encryption, federated learning systems that can maintain privacy and security guarantees even in the presence of quantum adversaries, and AI model authentication mechanisms that can verify the integrity and provenance of AI systems without relying on quantum-vulnerable digital signatures.
The challenge extends to protecting AI inference processes, securing AI-generated content, and maintaining the confidentiality of AI system architectures and parameters. Post-quantum cryptographic methods must be integrated throughout the AI development lifecycle, from initial research and development through deployment, operation, and maintenance of AI systems in production environments.
Hybrid Classical-Quantum Security Models
The transition to post-quantum cryptography will not occur instantaneously, creating a complex intermediate period where classical, quantum-resistant, and hybrid security models must coexist and interoperate effectively. This transitional landscape requires sophisticated approaches to cryptographic agility that can adapt to evolving quantum threats while maintaining compatibility with existing systems and infrastructure.
Hybrid security models combine multiple cryptographic approaches to provide defense-in-depth protection against both classical and quantum attacks. These systems may utilize classical cryptographic methods for compatibility with legacy systems while simultaneously implementing post-quantum algorithms for future-proofing against quantum threats. The challenge lies in ensuring that the security of hybrid systems is not compromised by the weakest component and that the combination of different cryptographic approaches provides genuine security benefits rather than introducing new vulnerabilities.
The development of cryptographic agility frameworks enables organizations to rapidly transition between different cryptographic algorithms and protocols as the threat landscape evolves. These frameworks must account for the unique challenges posed by AI-enhanced attacks, quantum computing capabilities, and the extended timeline required for widespread adoption of post-quantum cryptographic standards.
Enhance your research capabilities with Perplexity to stay informed about the rapidly evolving landscape of post-quantum cryptography standards, quantum computing developments, and AI security research that will shape the future of digital protection. The pace of advancement in these fields requires continuous monitoring and adaptation of security strategies.
Implementation Challenges and Performance Considerations
The practical deployment of post-quantum cryptographic systems presents significant technical challenges that must be addressed to ensure successful transition from current cryptographic infrastructure. These challenges encompass performance optimization, resource constraints, interoperability requirements, and the need to maintain security while adapting to diverse operational environments and use cases.
Post-quantum cryptographic algorithms typically require larger key sizes, increased computational resources, and more complex implementation procedures compared to traditional cryptographic methods. These resource requirements can be particularly challenging for resource-constrained environments such as Internet of Things devices, embedded systems, and mobile applications where computational power, memory, and battery life are limited.
The integration of AI optimization techniques offers potential solutions to some of these challenges by enabling more efficient implementations of post-quantum algorithms, optimizing cryptographic parameters for specific use cases, and developing adaptive security systems that can balance performance and security requirements based on real-time threat assessments and operational conditions.
Standardization and Regulatory Landscape
The development of post-quantum cryptographic standards represents a complex international effort involving government agencies, academic institutions, industry organizations, and standards bodies working to establish comprehensive frameworks for quantum-resistant security. The National Institute of Standards and Technology has led efforts to evaluate and standardize post-quantum cryptographic algorithms, while international organizations work to ensure global interoperability and adoption of quantum-safe cryptographic methods.
The regulatory implications of post-quantum cryptography extend beyond technical standards to encompass legal frameworks, compliance requirements, and policy considerations that will shape how organizations approach the quantum transition. Industries subject to strict regulatory oversight, including healthcare, finance, and government sectors, must navigate complex compliance landscapes while implementing quantum-resistant security measures.
The timeline for regulatory adoption of post-quantum cryptographic requirements varies significantly across jurisdictions and industries, creating challenges for multinational organizations that must comply with diverse regulatory frameworks while maintaining consistent security postures across their operations.
Economic and Strategic Implications
The transition to post-quantum cryptography represents a massive economic undertaking that will require substantial investments in research and development, infrastructure upgrades, personnel training, and system modernization across virtually every sector of the global economy. The costs associated with this transition include not only direct implementation expenses but also opportunity costs, business disruption, and the risks associated with delayed or inadequate preparation for quantum threats.
Organizations that successfully navigate the post-quantum transition may gain significant competitive advantages through enhanced security capabilities, customer trust, and regulatory compliance, while those that delay or inadequately prepare for quantum threats face potential catastrophic consequences including data breaches, financial losses, and regulatory penalties.
The strategic implications extend to national security considerations, as countries that achieve leadership in post-quantum cryptographic capabilities may gain significant advantages in intelligence gathering, cyber warfare capabilities, and protection of critical infrastructure. The development of quantum-safe AI systems becomes a matter of national strategic importance as artificial intelligence increasingly underpins economic competitiveness and military capabilities.
Future Research Directions and Emerging Threats
The field of post-quantum cryptography continues to evolve rapidly as researchers explore new mathematical foundations for quantum-resistant security, develop more efficient algorithms and implementation techniques, and investigate emerging threat vectors that could compromise quantum-safe systems. The integration of artificial intelligence into both cryptographic design and cryptanalytic capabilities creates a dynamic landscape where defensive and offensive capabilities continue to advance in parallel.
Emerging research areas include quantum-safe multi-party computation protocols that enable secure collaborative computing in the quantum era, post-quantum blockchain and distributed ledger technologies that can maintain security and integrity under quantum attacks, and adaptive cryptographic systems that can evolve and respond to new threats through machine learning and artificial intelligence capabilities.
The development of quantum error correction techniques and fault-tolerant quantum computing systems may alter the timeline and capabilities for practical quantum attacks, requiring continuous reassessment of post-quantum cryptographic security assumptions and the development of more sophisticated threat models that account for the evolving capabilities of quantum-AI hybrid systems.
Building Resilient Security Ecosystems
The creation of truly resilient security ecosystems for the post-quantum era requires comprehensive approaches that extend beyond cryptographic algorithms to encompass entire system architectures, operational procedures, and organizational cultures that prioritize security and adaptability. These ecosystems must be designed to withstand not only known quantum and AI-enhanced threats but also emerging attack vectors that have not yet been identified or fully understood.
Resilient security ecosystems incorporate principles of defense-in-depth, cryptographic agility, continuous monitoring and adaptation, and collaborative threat intelligence sharing that enable organizations to respond effectively to evolving security challenges. The integration of AI-powered security monitoring and response systems can provide enhanced capabilities for detecting and mitigating sophisticated attacks that combine quantum computing, artificial intelligence, and traditional attack techniques.
The development of these ecosystems requires close collaboration between cybersecurity professionals, quantum computing researchers, AI specialists, and domain experts who understand the specific security requirements and constraints of different industries and application areas. This multidisciplinary approach is essential for addressing the complex challenges posed by the convergence of quantum computing and artificial intelligence.
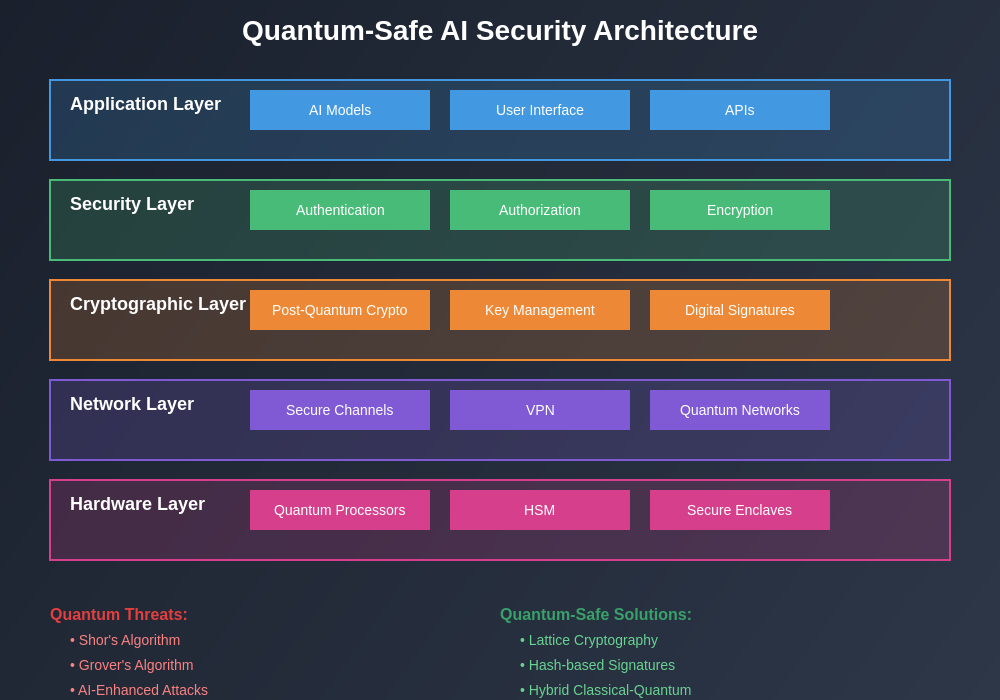
The layered security architecture for quantum-safe AI systems demonstrates the comprehensive approach required to protect against multiple threat vectors while maintaining system functionality and performance. Each layer provides specific security functions while integrating with adjacent layers to create defense-in-depth protection.
Preparing for the Post-Quantum Future
The transition to post-quantum cryptography represents one of the most significant technological migrations in the history of computing, requiring unprecedented coordination and preparation across government, industry, and academic sectors. Organizations must begin immediate preparation for this transition through comprehensive risk assessments, technology evaluations, staff training programs, and the development of migration strategies that can be implemented as quantum threats become more imminent.
The development of quantum-safe AI systems and the integration of post-quantum cryptographic methods into existing infrastructure cannot be delayed until quantum computers become capable of breaking current cryptographic systems. The complexity and scale of the required changes necessitate early action and sustained commitment to ensure that critical systems and sensitive data remain protected throughout the quantum transition period.
Success in navigating the post-quantum future will require not only technical expertise and technological investment but also strategic vision, organizational adaptability, and collaborative approaches that bring together diverse stakeholders in pursuit of common security objectives. The stakes could not be higher, as the security and privacy of our increasingly digital world depends on our collective ability to successfully transition to quantum-resistant cryptographic systems before practical quantum attacks become reality.
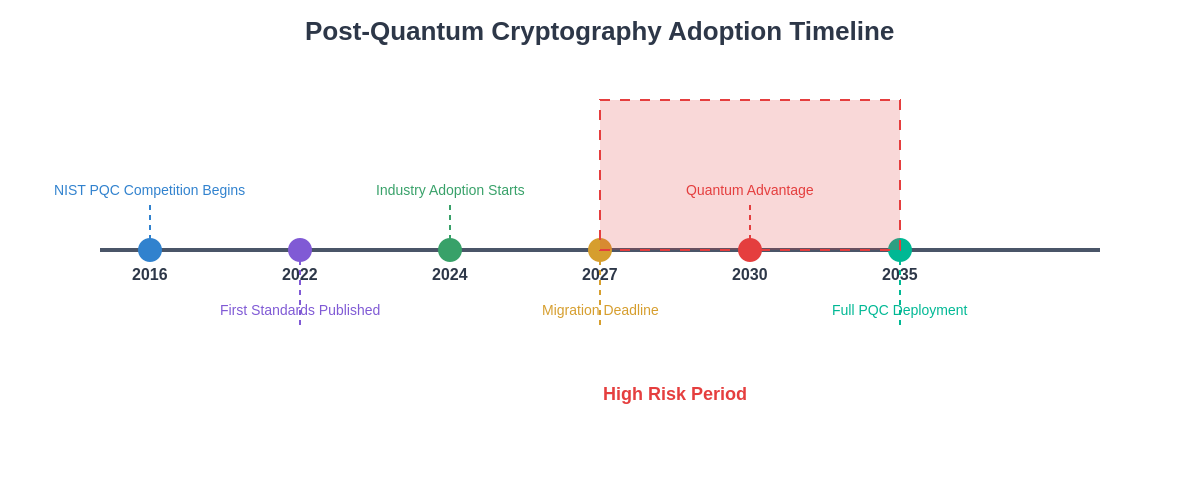
The post-quantum cryptography adoption timeline illustrates the critical phases of transition from current cryptographic systems to quantum-resistant alternatives. The highlighted high-risk period represents the window where quantum computing capabilities may outpace cryptographic defenses, emphasizing the urgency of proactive preparation and implementation.
Disclaimer
This article is for informational and educational purposes only and does not constitute professional security advice, cryptographic recommendations, or predictions about future technological developments. The field of post-quantum cryptography and quantum computing is rapidly evolving, and readers should consult with qualified security professionals and stay informed about the latest research and standardization efforts when making decisions about cryptographic implementations and security strategies. The effectiveness and security of post-quantum cryptographic methods may change as research progresses and new attack techniques are discovered.