In an era where data has become the most valuable commodity in the digital economy, organizations face an increasingly complex challenge: how to leverage the collective power of distributed datasets for artificial intelligence applications while maintaining absolute privacy and security of their sensitive information. Secure Multi-Party Computation represents a revolutionary cryptographic solution that enables multiple parties to jointly compute functions over their private inputs without revealing those inputs to each other, fundamentally transforming how collaborative artificial intelligence projects can be approached in privacy-sensitive environments.
Discover the latest privacy-preserving AI developments that are reshaping how organizations handle sensitive data in collaborative machine learning scenarios. The emergence of SMPC technologies has created unprecedented opportunities for cross-organizational collaboration while maintaining stringent privacy guarantees that were previously impossible to achieve through traditional data sharing approaches.
The Foundation of Privacy-Preserving Collaboration
Secure Multi-Party Computation emerges from decades of cryptographic research aimed at solving the fundamental problem of computing over distributed private data without compromising confidentiality. The core principle underlying SMPC protocols involves enabling multiple participants to collaboratively execute computations on their combined datasets while ensuring that no party learns anything about the other participants’ data beyond what can be inferred from the final computation result and their own input.
This cryptographic foundation has profound implications for artificial intelligence applications, where the quality and diversity of training data directly correlates with model performance and generalization capabilities. Traditional approaches to collaborative AI have required centralized data aggregation, creating single points of failure, privacy vulnerabilities, and regulatory compliance challenges that often prevent organizations from participating in potentially beneficial collaborative initiatives.
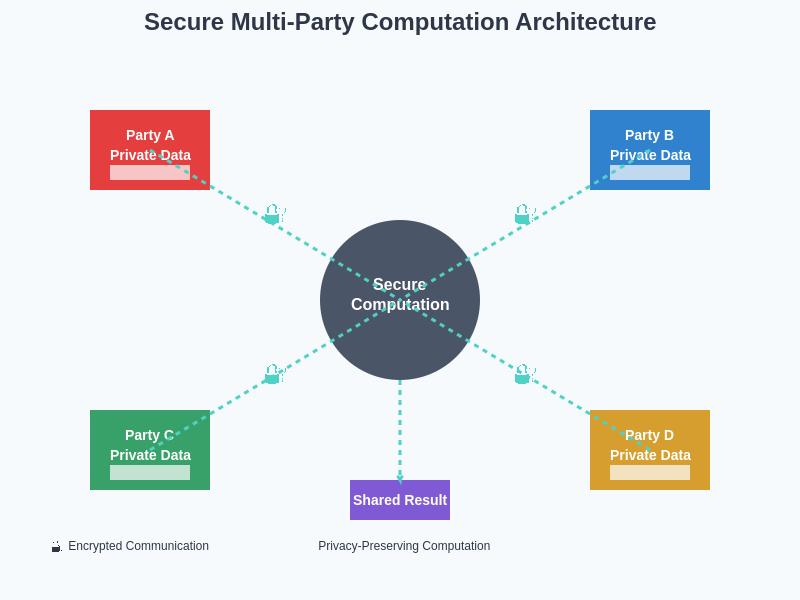
The architectural framework of Secure Multi-Party Computation demonstrates how multiple parties can contribute their private data to a collaborative computation without exposing sensitive information to other participants. This distributed approach eliminates single points of failure while maintaining cryptographic guarantees about data confidentiality throughout the entire computation process.
The mathematical elegance of SMPC protocols lies in their ability to distribute computational processes across multiple parties in such a way that the computation proceeds correctly while maintaining cryptographic guarantees about data privacy. These protocols typically involve secret sharing schemes, where sensitive data is divided into multiple shares distributed across participants, ensuring that no single party possesses sufficient information to reconstruct the original data without collaboration from other participants.
Cryptographic Mechanisms Enabling Secure Computation
The implementation of Secure Multi-Party Computation relies on sophisticated cryptographic primitives that work in concert to achieve the dual objectives of computational correctness and privacy preservation. Secret sharing schemes form the backbone of most SMPC protocols, utilizing mathematical techniques to divide sensitive information into multiple pieces, each of which reveals no information about the original data when examined in isolation.
Garbled circuits represent another fundamental component of SMPC implementations, particularly for scenarios involving boolean operations and general-purpose computation. These circuits enable the secure evaluation of arbitrary functions by encrypting the circuit structure in such a way that participants can execute computations without learning intermediate values or the specific logic being applied to their data.
Homomorphic encryption provides an additional layer of security by enabling computations to be performed directly on encrypted data, producing encrypted results that can be decrypted only by parties possessing the appropriate cryptographic keys. This approach is particularly valuable for mathematical operations common in machine learning algorithms, such as matrix multiplications, statistical aggregations, and optimization procedures.
Experience advanced privacy-preserving AI with Claude for sophisticated analysis and implementation guidance on complex cryptographic protocols. The integration of multiple cryptographic approaches within SMPC frameworks creates robust security guarantees that can withstand sophisticated adversarial attacks while maintaining computational efficiency suitable for practical applications.
Applications in Collaborative Machine Learning
The application of Secure Multi-Party Computation to collaborative machine learning scenarios has opened new possibilities for organizations that previously could not participate in joint AI initiatives due to privacy, regulatory, or competitive concerns. Healthcare organizations can now collaborate on developing diagnostic models using patient data from multiple institutions without exposing individual patient records or proprietary medical information to other participants.
Financial institutions can jointly develop fraud detection systems by combining their transaction datasets through SMPC protocols, creating more robust models that benefit from the diversity of attack patterns and customer behaviors across different institutions while maintaining strict confidentiality of customer information and proprietary business intelligence. This collaborative approach significantly enhances the effectiveness of fraud detection systems compared to models trained on individual institutional datasets.
The pharmaceutical industry has embraced SMPC technologies for drug discovery applications, where multiple research organizations can combine their molecular datasets, experimental results, and clinical trial data to accelerate the identification of promising therapeutic compounds. This collaboration occurs without exposing proprietary research data, trade secrets, or competitive advantages that organizations have invested significant resources to develop.
Government agencies and defense organizations utilize SMPC protocols for intelligence analysis and threat detection applications, where sensitive information from multiple sources must be analyzed collectively while maintaining strict classification levels and need-to-know restrictions. These applications demonstrate the versatility of SMPC approaches across diverse security requirements and operational constraints.
Technical Implementation Challenges and Solutions
The practical implementation of Secure Multi-Party Computation faces several significant technical challenges that must be addressed to achieve both security objectives and acceptable performance characteristics. Computational overhead represents one of the primary obstacles, as cryptographic operations required for secure computation typically impose substantial processing costs compared to equivalent plaintext computations.
Communication complexity presents another critical challenge, as SMPC protocols often require extensive information exchange between participants to maintain security guarantees while progressing through computational steps. Network latency, bandwidth limitations, and connection reliability can significantly impact the feasibility of SMPC applications in real-world scenarios with geographically distributed participants.
The scalability of SMPC protocols becomes increasingly complex as the number of participants grows, with many existing protocols experiencing exponential increases in computational and communication requirements. Research efforts have focused on developing more efficient protocols that can accommodate larger numbers of participants while maintaining acceptable performance characteristics for practical applications.
Security model assumptions present additional implementation challenges, as different SMPC protocols make varying assumptions about participant behavior, network security, and potential adversarial capabilities. Organizations must carefully evaluate these assumptions against their specific threat models and operational requirements to select appropriate protocol implementations.
Integration with Existing AI Infrastructure
The successful deployment of Secure Multi-Party Computation in collaborative AI scenarios requires careful integration with existing machine learning infrastructure, development workflows, and operational procedures. Organizations must adapt their data preprocessing pipelines to work with SMPC protocols while maintaining compatibility with existing model training and evaluation frameworks.
Performance optimization becomes critical when integrating SMPC capabilities, as the additional computational overhead can significantly impact training times and resource requirements for complex machine learning models. Hybrid approaches that combine SMPC protocols for sensitive operations with traditional computation for non-sensitive preprocessing and post-processing steps can provide optimal performance characteristics.
Data format standardization and protocol compatibility represent essential considerations for multi-organizational collaborations, as participants may use different technology stacks, data schemas, and security requirements. Establishing common interfaces and communication protocols ensures seamless integration across diverse organizational environments while maintaining security guarantees.
Enhance your research capabilities with Perplexity for comprehensive analysis of technical implementation details and best practices in privacy-preserving computation. The development of standardized frameworks and toolkits for SMPC implementation has accelerated adoption by providing organizations with tested, reliable implementations that can be integrated into existing systems with minimal custom development effort.
Privacy Guarantees and Threat Models
Understanding the precise privacy guarantees provided by different SMPC protocols is essential for organizations evaluating these technologies for sensitive applications. Computational privacy ensures that participants cannot learn information about other parties’ inputs during the execution of the secure computation protocol, even if they deviate from prescribed behavior within certain bounds defined by the security model.
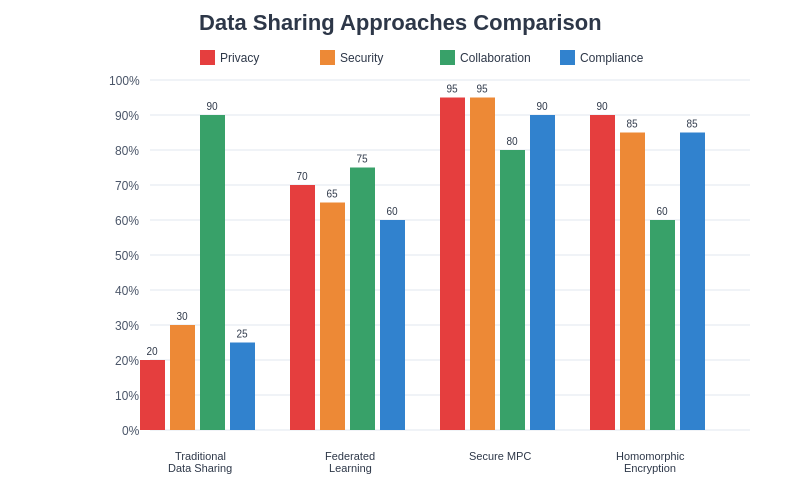
The comparative analysis of different privacy-preserving approaches reveals the superior security and privacy characteristics of Secure Multi-Party Computation compared to traditional data sharing methods, federated learning, and homomorphic encryption approaches. While SMPC may present some collaboration challenges due to its computational complexity, it provides unmatched privacy and security guarantees essential for sensitive applications.
Input privacy guarantees that the private data contributed by each participant remains confidential throughout the computation process, with formal mathematical proofs demonstrating that no information beyond what is revealed by the final result can be inferred by other participants. These guarantees hold even when participants attempt to extract additional information through sophisticated analysis of protocol communications and intermediate states.
Output privacy considerations address scenarios where the result of the secure computation itself might reveal sensitive information about participant inputs, requiring additional privacy-preserving techniques such as differential privacy or output perturbation to prevent inference attacks based on result analysis.
The robustness of privacy guarantees depends critically on the underlying threat model assumptions, including the number of participants that may collude, their computational capabilities, and their ability to deviate from protocol specifications. Semi-honest adversary models assume participants follow protocol instructions but may attempt to learn additional information from their observations, while malicious adversary models account for arbitrary deviations from prescribed behavior.
Performance Optimization and Scalability
Achieving practical performance in Secure Multi-Party Computation applications requires sophisticated optimization techniques that balance security requirements with computational efficiency. Protocol-level optimizations focus on reducing the number of communication rounds required for secure computation, minimizing the amount of data exchanged between participants, and optimizing cryptographic operations for specific hardware architectures.
Preprocessing techniques can significantly improve the online performance of SMPC protocols by performing computationally intensive operations in advance, before the actual private inputs are available. This approach separates the computation into offline and online phases, with the offline phase generating cryptographic material and computational shortcuts that enable rapid online execution when time-sensitive computations are required.
Parallel processing and distributed execution strategies help address scalability challenges by distributing computational workloads across multiple processors and systems within each participating organization. These approaches require careful coordination to maintain security guarantees while achieving performance improvements through parallelization.
Hardware acceleration through specialized cryptographic processors, graphics processing units, and custom silicon implementations can provide substantial performance improvements for specific SMPC operations. The development of dedicated hardware platforms optimized for privacy-preserving computation represents an active area of research and commercial development.
Regulatory Compliance and Legal Frameworks
The deployment of Secure Multi-Party Computation in regulated industries requires careful consideration of applicable legal frameworks, compliance requirements, and regulatory guidance. Data protection regulations such as the General Data Protection Regulation and various national privacy laws establish specific requirements for data processing, cross-border transfers, and privacy-by-design implementations that SMPC technologies can help address.
Healthcare regulations including the Health Insurance Portability and Accountability Act impose strict requirements on the handling of protected health information that can be satisfied through appropriately implemented SMPC protocols. The ability to perform collaborative analysis without exposing individual patient records provides significant advantages for healthcare organizations seeking to comply with privacy regulations while participating in research initiatives.
Financial services regulations governing customer data protection, anti-money laundering requirements, and cross-border data transfers can be addressed through SMPC implementations that enable compliance with multiple jurisdictional requirements simultaneously. The cryptographic guarantees provided by SMPC protocols often exceed the minimum requirements established by financial regulations, providing additional assurance for risk-averse organizations.
International data transfer restrictions and data localization requirements present complex compliance challenges that SMPC technologies can help address by enabling computation over distributed datasets without requiring physical data movement across jurisdictional boundaries. This capability is particularly valuable for multinational organizations operating in multiple regulatory jurisdictions with conflicting data residency requirements.
Industry-Specific Applications and Case Studies
The healthcare sector has emerged as one of the most promising application areas for Secure Multi-Party Computation, driven by the combination of valuable collaborative opportunities and strict privacy requirements. Multi-institutional clinical trials can leverage SMPC protocols to combine patient data across research sites without exposing individual patient information, enabling larger sample sizes and more robust statistical analyses while maintaining patient privacy and regulatory compliance.
Genomics research represents another healthcare application where SMPC technologies provide substantial benefits, allowing researchers to combine genetic datasets from multiple populations and institutions to identify disease associations and therapeutic targets without exposing sensitive genetic information. The scale and sensitivity of genomic data make traditional data sharing approaches impractical, while SMPC enables collaboration that would otherwise be impossible.
Financial services organizations have implemented SMPC solutions for collaborative fraud detection, where multiple banks and payment processors combine their transaction data to identify sophisticated fraud patterns that span multiple institutions. The ability to detect coordinated attacks and emerging fraud trends through secure collaboration provides significant advantages over isolated detection systems while protecting customer privacy and competitive information.
Telecommunications companies utilize SMPC protocols for network optimization and security applications, combining traffic data and threat intelligence across carriers to improve service quality and security postures without exposing proprietary network information or customer usage patterns. These collaborative approaches enable more effective responses to distributed attacks and network optimization opportunities.
Future Developments and Research Directions
The field of Secure Multi-Party Computation continues to evolve rapidly, with ongoing research focused on addressing current limitations and expanding the scope of practical applications. Quantum-resistant cryptographic protocols represent a critical research area, as the eventual development of practical quantum computers could compromise the security assumptions underlying current SMPC implementations.
Machine learning-specific optimizations for SMPC protocols aim to reduce the computational and communication overhead associated with common machine learning operations such as gradient descent, matrix factorization, and neural network training. These specialized protocols can achieve significantly better performance than general-purpose SMPC implementations by exploiting the mathematical structure of machine learning algorithms.
Federated learning integration with SMPC technologies creates hybrid approaches that combine the advantages of distributed model training with cryptographic privacy guarantees. These integrated approaches can provide enhanced privacy protection for federated learning scenarios while maintaining the scalability and efficiency advantages of federated approaches.
The development of standardized frameworks, APIs, and interoperability protocols will facilitate broader adoption of SMPC technologies by reducing implementation complexity and enabling seamless integration across different organizational systems and technology stacks. Industry consortiums and standards organizations are working to establish common specifications that will accelerate deployment and improve compatibility.
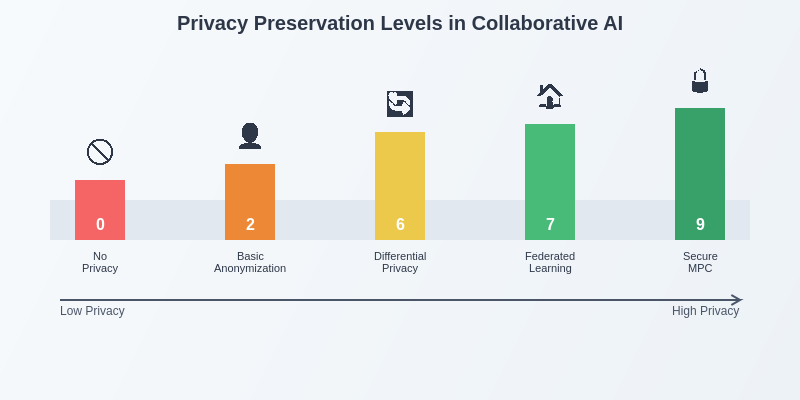
The spectrum of privacy preservation in collaborative AI demonstrates the evolutionary progression from basic data sharing approaches to sophisticated cryptographic solutions like Secure Multi-Party Computation. This visualization illustrates how SMPC represents the pinnacle of privacy-preserving collaboration, offering near-perfect confidentiality while enabling meaningful computational cooperation between organizations.
Economic and Strategic Implications
The adoption of Secure Multi-Party Computation technologies has significant economic implications for organizations seeking to monetize their data assets while maintaining competitive advantages and privacy obligations. SMPC enables new business models based on secure data collaboration, where organizations can participate in joint analytics initiatives and benefit from improved insights without losing control over their proprietary data.
The strategic value of SMPC technologies extends beyond immediate technical benefits to encompass competitive positioning and market differentiation opportunities. Organizations that develop capabilities in privacy-preserving collaboration can access new partnership opportunities, enter previously inaccessible markets, and offer innovative services that competitors cannot replicate without similar technical capabilities.
Cost-benefit analyses of SMPC implementations must consider both direct technical costs and indirect benefits such as reduced regulatory compliance costs, expanded collaboration opportunities, and enhanced reputation for privacy protection. The long-term strategic advantages often justify initial implementation investments, particularly for organizations in highly regulated or privacy-sensitive industries.
The emergence of SMPC-as-a-service platforms and specialized service providers is creating new market opportunities and reducing barriers to adoption for organizations that lack internal cryptographic expertise. These service models enable broader access to SMPC capabilities while providing specialized expertise and ongoing support for complex implementations.
Secure Multi-Party Computation represents a transformative technology that addresses one of the most fundamental challenges in the modern data economy: enabling collaborative computation while maintaining absolute privacy guarantees. As organizations increasingly recognize the value of collaborative AI initiatives and the importance of data privacy protection, SMPC technologies will continue to play a crucial role in shaping the future of privacy-preserving artificial intelligence and secure data collaboration across diverse industries and application domains.
Disclaimer
This article is for informational purposes only and does not constitute professional advice regarding cryptographic implementations, security protocols, or regulatory compliance. The views expressed are based on current understanding of secure computation technologies and their applications. Readers should consult with qualified cryptography experts and legal professionals when implementing privacy-preserving technologies. The effectiveness and security of SMPC implementations may vary depending on specific use cases, threat models, and implementation details.
