The evolution of artificial intelligence has ushered in a new era of biometric authentication technologies, with voice biometrics emerging as one of the most sophisticated and promising approaches to identity verification. This revolutionary technology leverages the unique characteristics of human speech patterns, vocal tract anatomy, and behavioral speaking habits to create highly secure authentication systems that are both convenient and remarkably accurate. Voice biometrics AI represents a convergence of advanced machine learning algorithms, signal processing techniques, and biometric science that is transforming how we approach security and identity verification across countless industries and applications.
Discover the latest AI trends in voice technology to understand how voice biometrics is shaping the future of authentication and security systems. The sophistication of modern voice biometric systems has reached a level where they can distinguish between identical twins, detect spoofing attempts, and maintain accuracy even when users have colds or other temporary voice alterations, making them increasingly valuable for high-security applications and everyday consumer use.
Understanding Voice Biometrics Technology
Voice biometrics technology operates on the fundamental principle that every individual possesses a unique vocal signature that encompasses both physiological and behavioral characteristics. The physiological aspects include the size and shape of the vocal tract, throat, nasal passages, and mouth cavity, which create distinctive resonance patterns and harmonic structures in speech. The behavioral components encompass speaking rhythm, accent patterns, pronunciation habits, and the way individuals construct and emphasize words and phrases during natural conversation.
Modern voice biometric systems employ sophisticated artificial intelligence algorithms to analyze hundreds of unique voice characteristics simultaneously, creating comprehensive voiceprints that serve as digital fingerprints for each individual. These systems examine acoustic features such as fundamental frequency patterns, formant distributions, spectral characteristics, and temporal dynamics of speech to build highly detailed biometric templates that can accurately identify speakers even in challenging acoustic environments or when speech samples are limited in duration.
The technology has evolved significantly from early speaker recognition systems that required controlled environments and extensive voice samples. Contemporary AI-powered voice biometrics can achieve remarkable accuracy with just a few seconds of natural speech, adapting to changes in voice characteristics over time while maintaining robust security against sophisticated spoofing attempts and environmental interference.
Core Components of Speaker Recognition Systems
The architecture of modern speaker recognition systems encompasses several sophisticated components that work in harmony to achieve accurate and reliable identification. The audio preprocessing module handles noise reduction, echo cancellation, and signal enhancement to ensure optimal voice quality for analysis. This component is crucial for maintaining system performance in real-world environments where background noise, poor audio quality, and varying recording conditions can significantly impact recognition accuracy.
Feature extraction represents the heart of voice biometric systems, where advanced algorithms analyze raw audio signals to identify and quantify the unique characteristics that distinguish one speaker from another. These systems examine multiple acoustic parameters including mel-frequency cepstral coefficients, linear predictive coding parameters, spectral features, and prosodic characteristics such as pitch, rhythm, and stress patterns that collectively create a comprehensive voice signature.
Experience advanced AI capabilities with Claude for developing sophisticated voice biometric applications that require complex pattern recognition and machine learning expertise. The machine learning engine utilizes deep neural networks, support vector machines, and ensemble methods to create robust classification models that can accurately match voice samples against enrolled voiceprints while continuously adapting to changes in speaker characteristics and environmental conditions.
Authentication Mechanisms and Security Protocols
Voice biometric authentication systems implement multiple layers of security protocols to ensure robust protection against unauthorized access attempts and sophisticated spoofing attacks. The enrollment phase captures multiple voice samples from authorized users under various conditions to create comprehensive baseline voiceprints that account for natural variations in speech patterns, emotional states, and environmental factors that might affect voice characteristics during normal use.
The authentication process employs real-time analysis techniques that compare incoming voice samples against stored voiceprints using advanced matching algorithms that can accommodate natural variations while detecting anomalies that might indicate fraudulent access attempts. These systems incorporate liveness detection mechanisms that verify the presence of a live speaker rather than recorded audio, using techniques such as challenge-response protocols, acoustic environment analysis, and temporal speech pattern verification.
Modern voice biometric systems also implement continuous authentication capabilities that monitor voice characteristics throughout extended sessions, providing ongoing verification that the authenticated user remains the same person throughout the interaction. This approach is particularly valuable for high-security applications where maintaining identity verification over extended periods is crucial for maintaining system integrity and preventing unauthorized access during active sessions.
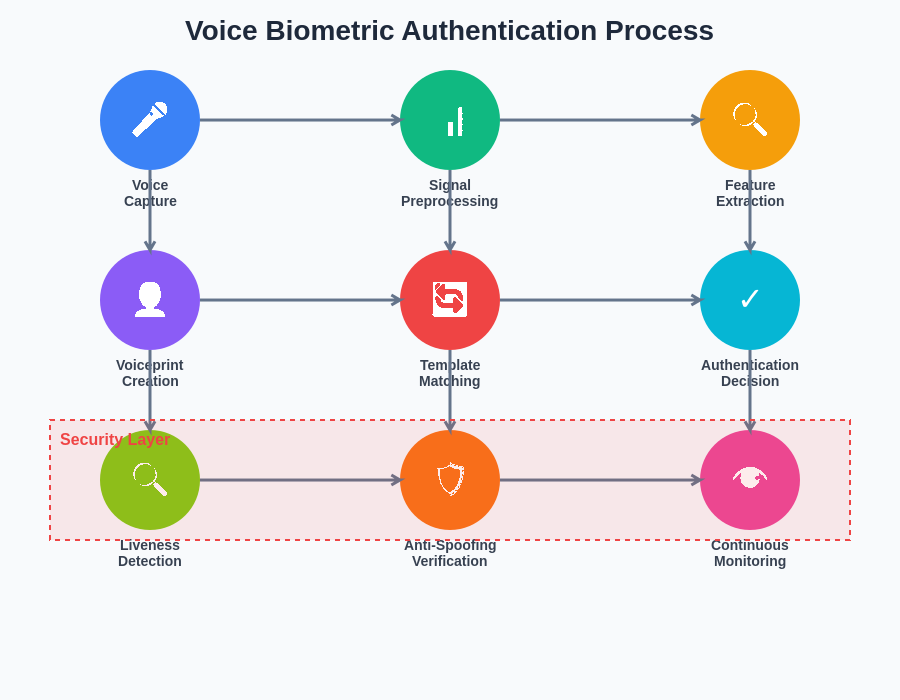
The sophisticated multi-stage authentication process ensures comprehensive security while maintaining user convenience through seamless voice-based verification that adapts to natural speech variations and environmental conditions.
Applications Across Industries and Sectors
The versatility and security advantages of voice biometrics have led to widespread adoption across numerous industries and application domains. Financial services organizations utilize voice biometric authentication for telephone banking, mobile payment verification, and secure account access, providing customers with convenient authentication methods while maintaining the highest security standards for financial transactions and sensitive account information.
Healthcare systems implement voice biometrics for secure access to electronic health records, medication dispensing systems, and telemedicine platforms, ensuring that only authorized medical personnel can access patient information while streamlining workflows in high-pressure medical environments. The technology proves particularly valuable in sterile environments where traditional authentication methods like fingerprint scanners or keyboards might compromise hygiene protocols.
Law enforcement and forensic applications leverage voice biometrics for criminal identification, witness verification, and evidence analysis, utilizing advanced speaker recognition capabilities to support investigations and legal proceedings. These systems can analyze recorded conversations, identify speakers in multi-party discussions, and provide expert testimony regarding voice identification in criminal cases where speaker identity is crucial for establishing facts and supporting legal arguments.
Government and military organizations employ voice biometrics for secure facility access, classified information systems, and personnel verification in high-security environments where robust authentication is essential for national security. The technology provides remote authentication capabilities that are particularly valuable for field operations and distributed security systems where traditional biometric methods might be impractical or compromised.
Technical Challenges and Advanced Solutions
The development and deployment of voice biometric systems face numerous technical challenges that require sophisticated solutions and continuous innovation. Environmental noise interference represents one of the most significant obstacles, as background sounds, poor audio quality, and varying acoustic conditions can significantly impact system performance and accuracy. Advanced noise reduction algorithms, adaptive filtering techniques, and robust feature extraction methods have been developed to maintain high performance even in challenging acoustic environments.
Voice spoofing and presentation attacks pose serious security concerns for voice biometric systems, as malicious actors may attempt to use recorded audio, synthetic speech, or voice conversion techniques to bypass authentication mechanisms. Modern systems implement comprehensive anti-spoofing measures including liveness detection, acoustic environment analysis, and behavioral pattern verification that can detect and prevent various types of spoofing attempts while maintaining user convenience and system usability.
Explore comprehensive AI research with Perplexity to stay updated on the latest advances in voice biometric security and anti-spoofing technologies. The challenge of handling voice changes due to aging, illness, emotional states, or medical conditions requires adaptive algorithms that can accommodate natural variations in voice characteristics while maintaining security and accuracy. Machine learning models continuously update voiceprint templates to reflect gradual changes while detecting significant deviations that might indicate security threats or system compromise.
Privacy and Ethical Considerations
The implementation of voice biometric systems raises important privacy and ethical considerations that must be carefully addressed to ensure responsible deployment and user acceptance. Voice samples contain rich information about individuals including emotional states, health conditions, and personal characteristics that extend beyond simple identity verification, requiring robust data protection measures and clear privacy policies that govern how voice data is collected, stored, and utilized.
Consent and transparency represent fundamental requirements for voice biometric systems, as users must clearly understand how their voice data will be used, stored, and protected. Organizations implementing voice biometrics must provide comprehensive information about data collection practices, retention policies, and sharing arrangements while obtaining explicit consent for voice data processing and biometric template creation.
The potential for voice data to be used for purposes beyond its original intent requires careful consideration of data minimization principles and purpose limitation safeguards. Voice biometric systems should collect only the minimum voice data necessary for authentication purposes and implement strong access controls and audit mechanisms to prevent unauthorized use or disclosure of sensitive biometric information.
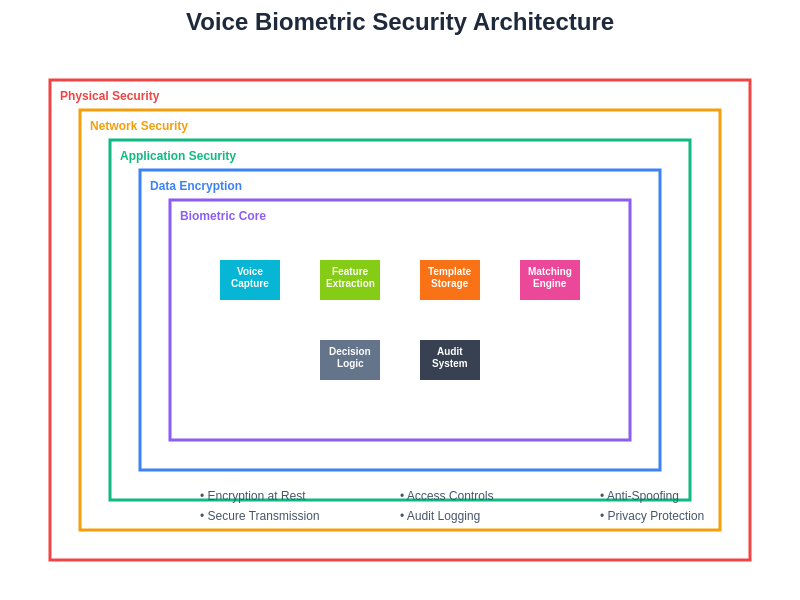
The comprehensive security framework addresses multiple layers of protection from voice capture and processing through template storage and matching, ensuring robust privacy protection while maintaining system effectiveness.
Performance Metrics and Accuracy Standards
The evaluation of voice biometric systems relies on several key performance metrics that measure accuracy, security, and usability across different operating conditions and user populations. False Acceptance Rate measures the frequency with which unauthorized users are incorrectly granted access, while False Rejection Rate quantifies how often legitimate users are incorrectly denied access. The Equal Error Rate represents the point where these two error rates intersect, providing a balanced measure of overall system performance.
Recognition accuracy varies significantly based on factors such as voice sample duration, audio quality, environmental conditions, and individual speaker characteristics. High-quality voice biometric systems typically achieve accuracy rates exceeding ninety-nine percent under optimal conditions, with performance remaining robust even when dealing with shorter voice samples or challenging acoustic environments that might compromise other biometric modalities.
Usability metrics encompass factors such as enrollment time, authentication speed, and user acceptance rates that determine the practical effectiveness of voice biometric systems in real-world applications. Modern systems can complete authentication in seconds while requiring minimal user training or technical expertise, making voice biometrics highly suitable for applications where user convenience and accessibility are important considerations.
Integration with Multi-Modal Biometric Systems
The combination of voice biometrics with other biometric modalities creates powerful multi-modal authentication systems that provide enhanced security, improved accuracy, and greater flexibility for diverse application requirements. Face recognition systems complement voice biometrics by providing visual verification that works effectively in quiet environments where voice authentication might be inappropriate or compromised by ambient noise conditions.
Fingerprint and palm print biometrics offer additional verification layers that can be combined with voice authentication to create highly secure systems suitable for applications requiring the highest levels of security assurance. The fusion of multiple biometric modalities provides redundancy that ensures system functionality even when individual modalities are temporarily unavailable or compromised by environmental conditions or user circumstances.
Behavioral biometrics such as typing patterns, gait analysis, and device interaction behaviors can be seamlessly integrated with voice biometrics to create comprehensive identity verification systems that continuously monitor user behavior and detect anomalies that might indicate security threats or unauthorized access attempts. This holistic approach to biometric authentication provides robust security while maintaining user convenience and system usability.
Future Technological Developments
The future of voice biometric technology promises exciting developments driven by advances in artificial intelligence, machine learning, and signal processing techniques. Deep learning architectures continue to improve the accuracy and robustness of speaker recognition systems while reducing computational requirements and enabling deployment on mobile devices and edge computing platforms that bring biometric capabilities directly to users without requiring cloud connectivity.
Federated learning approaches enable voice biometric systems to improve performance through collaborative learning while maintaining privacy and data protection by keeping voice data localized and sharing only model updates rather than raw biometric information. This approach addresses privacy concerns while enabling continuous improvement of recognition algorithms through exposure to diverse voice samples and operating conditions.
The integration of emotion recognition and sentiment analysis capabilities with voice biometrics creates opportunities for enhanced user experience and additional security layers that can detect stress, deception, or other behavioral indicators that might suggest security threats or unauthorized access attempts. These advanced capabilities extend voice biometric applications beyond simple authentication to comprehensive behavioral analysis and risk assessment.
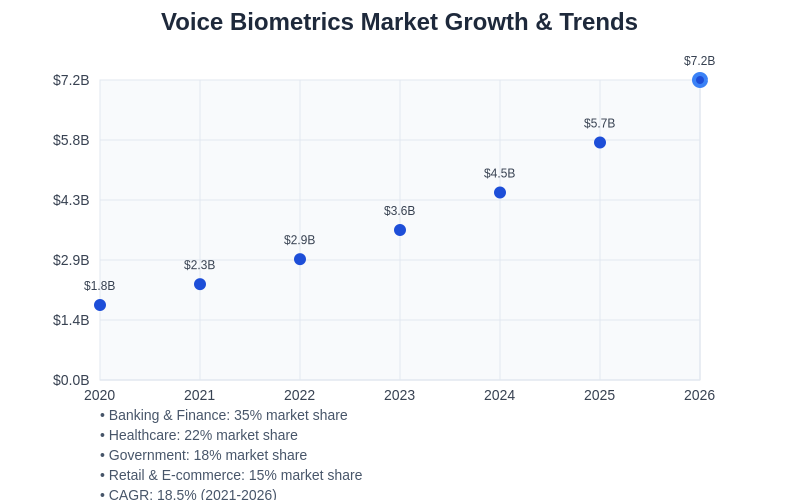
The rapid growth and technological advancement in voice biometrics reflects increasing demand for secure, convenient authentication solutions across multiple industries and application domains.
Implementation Best Practices
Successful deployment of voice biometric systems requires careful attention to technical implementation details, user experience design, and operational considerations that ensure optimal performance and user acceptance. System design should accommodate the diverse acoustic environments and user populations that will interact with the technology, incorporating adaptive algorithms and robust preprocessing capabilities that maintain performance across varying conditions.
User enrollment processes should be designed to capture representative voice samples that account for natural variations in speech patterns while providing clear guidance and feedback to ensure high-quality voiceprint creation. Multiple enrollment sessions conducted under different conditions can improve system robustness and accommodate users who may have difficulty with initial enrollment due to temporary voice changes or environmental factors.
Regular system maintenance and performance monitoring ensure continued accuracy and security through ongoing calibration, algorithm updates, and security assessments that identify and address potential vulnerabilities or performance degradation. Comprehensive logging and audit capabilities provide visibility into system operation and support forensic analysis when security incidents or disputes arise regarding authentication decisions.
Economic Impact and Market Dynamics
The voice biometrics market has experienced rapid growth driven by increasing demand for secure authentication solutions, advances in artificial intelligence technology, and growing awareness of the limitations and vulnerabilities associated with traditional password-based security systems. Organizations across industries recognize the economic benefits of voice biometric authentication including reduced support costs for password resets, improved user experience leading to higher customer satisfaction, and enhanced security that reduces the risk of costly data breaches and fraud.
The cost-effectiveness of voice biometric systems compared to other biometric modalities makes them attractive for applications where deployment costs and infrastructure requirements are important considerations. Voice authentication requires only basic audio capture capabilities that are readily available in most modern devices, eliminating the need for specialized hardware investments that other biometric modalities might require.
Return on investment for voice biometric implementations typically includes quantifiable benefits such as reduced authentication-related support costs, improved operational efficiency through faster user verification, and enhanced security that reduces fraud losses and compliance violations. These tangible benefits, combined with improved user satisfaction and competitive advantages, create compelling business cases for voice biometric adoption across diverse industries and applications.
Regulatory Compliance and Standards
The deployment of voice biometric systems must comply with various regulatory requirements and industry standards that govern biometric data collection, processing, and storage. Privacy regulations such as the General Data Protection Regulation and various national privacy laws establish strict requirements for consent, data minimization, and user rights that organizations must address when implementing voice biometric authentication systems.
Industry-specific regulations in sectors such as financial services, healthcare, and government create additional compliance requirements that voice biometric systems must satisfy while maintaining security and functionality. These regulations often specify technical standards, audit requirements, and data protection measures that must be incorporated into system design and operational procedures.
International standards organizations have developed comprehensive guidelines and technical specifications for biometric systems that provide frameworks for ensuring interoperability, security, and quality across different implementations and vendors. Compliance with these standards helps organizations ensure that their voice biometric systems meet industry best practices and provide reliable, secure authentication capabilities that can be trusted for critical applications.
Conclusion and Future Outlook
Voice biometric technology represents a transformative approach to identity verification and authentication that combines advanced artificial intelligence with the unique characteristics of human speech to create secure, convenient, and highly accurate authentication systems. The continued evolution of machine learning algorithms, signal processing techniques, and hardware capabilities promises even greater capabilities and broader applications for voice biometric technology in the coming years.
The integration of voice biometrics with emerging technologies such as Internet of Things devices, smart home systems, and autonomous vehicles creates new opportunities for seamless, secure authentication that enhances user experience while maintaining robust security. As these technologies mature and become more widely adopted, voice biometrics will play an increasingly important role in creating secure, connected environments that protect privacy while enabling convenient access to digital services and resources.
The future success of voice biometric technology will depend on continued innovation in addressing technical challenges, maintaining user privacy and security, and developing standards and best practices that ensure responsible deployment across diverse applications and industries. Organizations that embrace voice biometric technology while addressing these considerations will be well-positioned to benefit from the enhanced security, improved user experience, and operational efficiencies that this revolutionary technology provides.
Disclaimer
This article is for informational purposes only and does not constitute professional advice regarding security implementations or biometric technology deployment. The information presented reflects current understanding of voice biometric technologies and their applications, but readers should conduct thorough research and consult with qualified professionals before implementing biometric authentication systems. The effectiveness and suitability of voice biometric solutions may vary depending on specific requirements, regulatory environments, and operational constraints. Security implementations should always be evaluated by qualified security professionals to ensure adequate protection for specific use cases and risk profiles.